312-50 : CEH Certified Ethical Hacker (312-50v9) : Part 01
-
Which of the following is a hardware requirement that either an IDS/IPS system or a proxy server must have in order to properly function?
- Fast processor to help with network traffic analysis
- They must be dual-homed
- Similar RAM requirements
- Fast network interface cards
Explanation:
Dual-homed or dual-homing can refer to either an Ethernet device that has more than one network interface, for redundancy purposes, or in firewall technology, dual-homed is one of the firewall architectures, such as an IDS/IPS system, for implementing preventive security.
-
Which of the following is an application that requires a host application for replication?
- Micro
- Worm
- Trojan
- Virus
Explanation:
Computer viruses infect a variety of different subsystems on their hosts. A computer virus is a malware that, when executed, replicates by reproducing it self or infecting other programs by modifying them. Infecting computer programs can include as well, data files, or the boot sector of the hard drive. When this replication succeeds, the affected areas are then said to be “infected”.
-
A large company intends to use Blackberry for corporate mobile phones and a security analyst is assigned to evaluate the possible threats. The analyst will use the Blackjacking attack method to demonstrate how an attacker could circumvent perimeter defenses and gain access to the corporate network. What tool should the analyst use to perform a Blackjacking attack?
- Paros Proxy
- BBProxy
- BBCrack
- Blooover
Explanation:
Blackberry users warned of hacking tool threat.
Users have been warned that the security of Blackberry wireless e-mail devices is at risk due to the availability this week of a new hacking tool. Secure Computing Corporation said businesses that have installed Blackberry servers behind their gateway security devices could be vulnerable to a hacking attack from a tool call BBProxy. -
Which of the following can the administrator do to verify that a tape backup can be recovered in its entirety?
- Restore a random file.
- Perform a full restore.
- Read the first 512 bytes of the tape.
- Read the last 512 bytes of the tape.
Explanation:
A full restore is required.
-
Which of the following describes the characteristics of a Boot Sector Virus?
- Moves the MBR to another location on the RAM and copies itself to the original location of the MBR
- Moves the MBR to another location on the hard disk and copies itself to the original location of the MBR
- Modifies directory table entries so that directory entries point to the virus code instead of the actual program
- Overwrites the original MBR and only executes the new virus code
A boot sector virus is a computer virus that infects a storage device’s master boot record (MBR). The virus moves the boot sector to another location on the hard drive.
-
Which statement is TRUE regarding network firewalls preventing Web Application attacks?
- Network firewalls can prevent attacks because they can detect malicious HTTP traffic.
- Network firewalls cannot prevent attacks because ports 80 and 443 must be opened.
- Network firewalls can prevent attacks if they are properly configured.
- Network firewalls cannot prevent attacks because they are too complex to configure.
Explanation:
Network layer firewalls, also called packet filters, operate at a relatively low level of the TCP/IP protocol stack, not allowing packets to pass through the firewall unless they match the established rule set. To prevent Web Application attacks an Application layer firewall would be required.
-
Which of the following programs is usually targeted at Microsoft Office products?
- Polymorphic virus
- Multipart virus
- Macro virus
- Stealth virus
Explanation:
A macro virus is a virus that is written in a macro language: a programming language which is embedded inside a software application (e.g., word processors and spreadsheet applications). Some applications, such as Microsoft Office, allow macro programs to be embedded in documents such that the macros are run automatically when the document is opened, and this provides a distinct mechanism by which malicious computer instructions can spread.
-
Bluetooth uses which digital modulation technique to exchange information between paired devices?
- PSK (phase-shift keying)
- FSK (frequency-shift keying)
- ASK (amplitude-shift keying)
- QAM (quadrature amplitude modulation)
Explanation:
Phase shift keying is the form of Bluetooth modulation used to enable the higher data rates achievable with Bluetooth 2 EDR (Enhanced Data Rate). Two forms of PSK are used: π/4 DQPSK, and 8DPSK.
-
In order to show improvement of security over time, what must be developed?
- Reports
- Testing tools
- Metrics
- Taxonomy of vulnerabilities
-
Passive reconnaissance involves collecting information through which of the following?
- Social engineering
- Network traffic sniffing
- Man in the middle attacks
- Publicly accessible sources
-
How can rainbow tables be defeated?
- Password salting
- Use of non-dictionary words
- All uppercase character passwords
- Lockout accounts under brute force password cracking attempts
-
The following is a sample of output from a penetration tester’s machine targeting a machine with the IP address of 192.168.1.106:
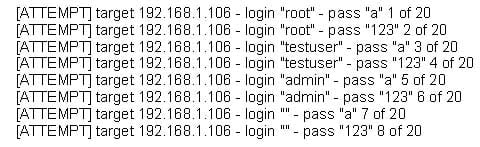
312-50 Part 1 Q12 001 What is most likely taking place?
- Ping sweep of the 192.168.1.106 network
- Remote service brute force attempt
- Port scan of 192.168.1.106
- Denial of service attack on 192.168.1.106
-
An NMAP scan of a server shows port 25 is open. What risk could this pose?
- Open printer sharing
- Web portal data leak
- Clear text authentication
- Active mail relay
-
A penetration tester is conducting a port scan on a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed. Considering the NMAP result below, which of the following is likely to be installed on the target machine by the OS?
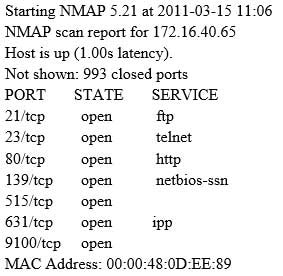
312-50 Part 1 Q14 002 - The host is likely a Windows machine.
- The host is likely a Linux machine.
- The host is likely a router.
- The host is likely a printer.
-
What type of OS fingerprinting technique sends specially crafted packets to the remote OS and analyzes the received response?
- Passive
- Reflective
- Active
- Distributive
-
Which of the following lists are valid data-gathering activities associated with a risk assessment?
- Threat identification, vulnerability identification, control analysis
- Threat identification, response identification, mitigation identification
- Attack profile, defense profile, loss profile
- System profile, vulnerability identification, security determination
-
A penetration tester is hired to do a risk assessment of a company’s DMZ. The rules of engagement states that the penetration test be done from an external IP address with no prior knowledge of the internal IT systems. What kind of test is being performed?
- white box
- grey box
- red box
- black box
-
Which of the following is a detective control?
- Smart card authentication
- Security policy
- Audit trail
- Continuity of operations plan
-
Which of the following is a component of a risk assessment?
- Physical security
- Administrative safeguards
- DMZ
- Logical interface
-
When utilizing technical assessment methods to assess the security posture of a network, which of the following techniques would be most effective in determining whether end-user security training would be beneficial?
- Vulnerability scanning
- Social engineering
- Application security testing
- Network sniffing