312-50 : CEH Certified Ethical Hacker (312-50v9) : Part 02
-
A company has publicly hosted web applications and an internal Intranet protected by a firewall. Which technique will help protect against enumeration?
- Reject all invalid email received via SMTP.
- Allow full DNS zone transfers.
- Remove A records for internal hosts.
- Enable null session pipes.
-
Which of the following techniques will identify if computer files have been changed?
- Network sniffing
- Permission sets
- Integrity checking hashes
- Firewall alerts
-
Which system consists of a publicly available set of databases that contain domain name registration contact information?
- WHOIS
- IANA
- CAPTCHA
- IETF
-
A penetration tester was hired to perform a penetration test for a bank. The tester began searching for IP ranges owned by the bank, performing lookups on the bank’s DNS servers, reading news articles online about the bank, watching what times the bank employees come into work and leave from work, searching the bank’s job postings (paying special attention to IT related jobs), and visiting the local dumpster for the bank’s corporate office. What phase of the penetration test is the tester currently in?
- Information reporting
- Vulnerability assessment
- Active information gathering
- Passive information gathering
-
The following is part of a log file taken from the machine on the network with the IP address of 192.168.1.106:
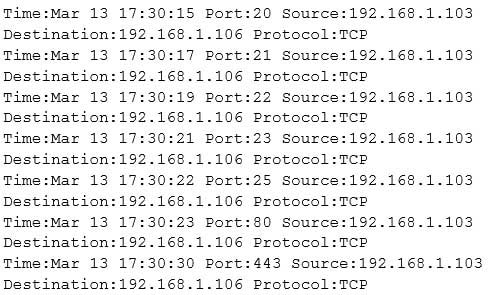
312-50 Part 2 Q05 003 What type of activity has been logged?
- Port scan targeting 192.168.1.103
- Teardrop attack targeting 192.168.1.106
- Denial of service attack targeting 192.168.1.103
- Port scan targeting 192.168.1.106
-
A Security Engineer at a medium-sized accounting firm has been tasked with discovering how much information can be obtained from the firm’s public facing web servers. The engineer decides to start by using netcat to port 80.
The engineer receives this output: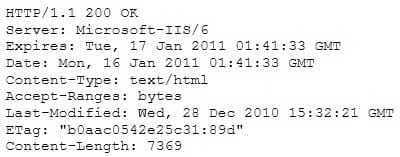
312-50 Part 2 Q06 004 Which of the following is an example of what the engineer performed?
- Cross-site scripting
- Banner grabbing
- SQL injection
- Whois database query
-
An NMAP scan of a server shows port 69 is open. What risk could this pose?
- Unauthenticated access
- Weak SSL version
- Cleartext login
- Web portal data leak
-
What information should an IT system analysis provide to the risk assessor?
- Management buy-in
- Threat statement
- Security architecture
- Impact analysis
-
Which results will be returned with the following Google search query?
site:target.com -site:Marketing.target.com accounting
- Results matching all words in the query
- Results matching “accounting” in domain target.com but not on the site Marketing.target.com
- Results from matches on the site marketing.target.com that are in the domain target.com but do not include the word accounting
- Results for matches on target.com and Marketing.target.com that include the word “accounting”
-
A bank stores and processes sensitive privacy information related to home loans. However, auditing has never been enabled on the system. What is the first step that the bank should take before enabling the audit feature?
- Perform a vulnerability scan of the system.
- Determine the impact of enabling the audit feature.
- Perform a cost/benefit analysis of the audit feature.
- Allocate funds for staffing of audit log review.
-
Which of the following is a preventive control?
- Smart card authentication
- Security policy
- Audit trail
- Continuity of operations plan
-
Which of the following is considered an acceptable option when managing a risk?
- Reject the risk.
- Deny the risk.
- Mitigate the risk.
- Initiate the risk.
-
Which security control role does encryption meet?
- Preventative
- Detective
- Offensive
- Defensive
-
A covert channel is a channel that
- transfers information over, within a computer system, or network that is outside of the security policy.
- transfers information over, within a computer system, or network that is within the security policy.
- transfers information via a communication path within a computer system, or network for transfer of data.
- transfers information over, within a computer system, or network that is encrypted.
-
John the Ripper is a technical assessment tool used to test the weakness of which of the following?
- Usernames
- File permissions
- Firewall rulesets
- Passwords
-
Least privilege is a security concept that requires that a user is
- limited to those functions required to do the job.
- given root or administrative privileges.
- trusted to keep all data and access to that data under their sole control.
- given privileges equal to everyone else in the department.
-
If the final set of security controls does not eliminate all risk in a system, what could be done next?
- Continue to apply controls until there is zero risk.
- Ignore any remaining risk.
- If the residual risk is low enough, it can be accepted.
- Remove current controls since they are not completely effective.
-
What is one thing a tester can do to ensure that the software is trusted and is not changing or tampering with critical data on the back end of a system it is loaded on?
- Proper testing
- Secure coding principles
- Systems security and architecture review
- Analysis of interrupts within the software
-
Which of the following examples best represents a logical or technical control?
- Security tokens
- Heating and air conditioning
- Smoke and fire alarms
- Corporate security policy
-
Which type of access control is used on a router or firewall to limit network activity?
- Mandatory
- Discretionary
- Rule-based
- Role-based
Subscribe
0 Comments
Newest