312-50 : CEH Certified Ethical Hacker (312-50v9) : Part 04
-
Which type of scan is used on the eye to measure the layer of blood vessels?
- Facial recognition scan
- Retinal scan
- Iris scan
- Signature kinetics scan
-
What is the main reason the use of a stored biometric is vulnerable to an attack?
- The digital representation of the biometric might not be unique, even if the physical characteristic is unique.
- Authentication using a stored biometric compares a copy to a copy instead of the original to a copy.
- A stored biometric is no longer “something you are” and instead becomes “something you have”.
- A stored biometric can be stolen and used by an attacker to impersonate the individual identified by the biometric.
-
During a wireless penetration test, a tester detects an access point using WPA2 encryption. Which of the following attacks should be used to obtain the key?
- The tester must capture the WPA2 authentication handshake and then crack it.
- The tester must use the tool inSSIDer to crack it using the ESSID of the network.
- The tester cannot crack WPA2 because it is in full compliance with the IEEE 802.11i standard.
- The tester must change the MAC address of the wireless network card and then use the AirTraf tool to obtain the key.
-
Which type of antenna is used in wireless communication?
- Omnidirectional
- Parabolic
- Uni-directional
- Bi-directional
-
What is the name of the international standard that establishes a baseline level of confidence in the security functionality of IT products by providing a set of requirements for evaluation?
- Blue Book
- ISO 26029
- Common Criteria
- The Wassenaar Agreement
-
One way to defeat a multi-level security solution is to leak data via
- a bypass regulator.
- steganography.
- a covert channel.
- asymmetric routing.
-
Which of the following conditions must be given to allow a tester to exploit a Cross-Site Request Forgery (CSRF) vulnerable web application?
- The victim user must open the malicious link with an Internet Explorer prior to version 8.
- The session cookies generated by the application do not have the HttpOnly flag set.
- The victim user must open the malicious link with a Firefox prior to version 3.
- The web application should not use random tokens.
-
What is the main difference between a “Normal” SQL Injection and a “Blind” SQL Injection vulnerability?
- The request to the web server is not visible to the administrator of the vulnerable application.
- The attack is called “Blind” because, although the application properly filters user input, it is still vulnerable to code injection.
- The successful attack does not show an error message to the administrator of the affected application.
- The vulnerable application does not display errors with information about the injection results to the attacker.
-
During a penetration test, a tester finds a target that is running MS SQL 2000 with default credentials. The tester assumes that the service is running with Local System account. How can this weakness be exploited to access the system?
- Using the Metasploit psexec module setting the SA / Admin credential
- Invoking the stored procedure xp_shell to spawn a Windows command shell
- Invoking the stored procedure cmd_shell to spawn a Windows command shell
- Invoking the stored procedure xp_cmdshell to spawn a Windows command shell
-
The precaution of prohibiting employees from bringing personal computing devices into a facility is what type of security control?
- Physical
- Procedural
- Technical
- Compliance
-
A pentester gains access to a Windows application server and needs to determine the settings of the built-in Windows firewall. Which command would be used?
- Netsh firewall show config
- WMIC firewall show config
- Net firewall show config
- Ipconfig firewall show config
-
Which of the following types of firewall inspects only header information in network traffic?
- Packet filter
- Stateful inspection
- Circuit-level gateway
- Application-level gateway
-
During a penetration test, the tester conducts an ACK scan using NMAP against the external interface of the DMZ firewall. NMAP reports that port 80 is unfiltered. Based on this response, which type of packet inspection is the firewall conducting?
- Host
- Stateful
- Stateless
- Application
-
Firewalk has just completed the second phase (the scanning phase) and a technician receives the output shown below. What conclusions can be drawn based on these scan results?

312-50 Part 4 Q14 006 - The firewall itself is blocking ports 21 through 23 and a service is listening on port 23 of the target host.
- The lack of response from ports 21 and 22 indicate that those services are not running on the destination server.
- The scan on port 23 passed through the filtering device. This indicates that port 23 was not blocked at the firewall.
- The scan on port 23 was able to make a connection to the destination host prompting the firewall to respond with a TTL error.
-
Which of the following is an example of an asymmetric encryption implementation?
- SHA1
- PGP
- 3DES
- MD5
-
A hacker was able to sniff packets on a company’s wireless network. The following information was discovered:
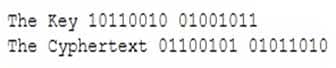
312-50 Part 4 Q16 007 Using the Exlcusive OR, what was the original message?
- 00101000 11101110
- 11010111 00010001
- 00001101 10100100
- 11110010 01011011
-
Which of the following cryptography attack methods is usually performed without the use of a computer?
- Ciphertext-only attack
- Chosen key attack
- Rubber hose attack
- Rainbow table attack
-
Which of the following is a strong post designed to stop a car?
- Gate
- Fence
- Bollard
- Reinforced rebar
-
A Network Administrator was recently promoted to Chief Security Officer at a local university. One of employee’s new responsibilities is to manage the implementation of an RFID card access system to a new server room on campus. The server room will house student enrollment information that is securely backed up to an off-site location.
During a meeting with an outside consultant, the Chief Security Officer explains that he is concerned that the existing security controls have not been designed properly. Currently, the Network Administrator is responsible for approving and issuing RFID card access to the server room, as well as reviewing the electronic access logs on a weekly basis.
Which of the following is an issue with the situation?
- Segregation of duties
- Undue influence
- Lack of experience
- Inadequate disaster recovery plan
-
What is the most secure way to mitigate the theft of corporate information from a laptop that was left in a hotel room?
- Set a BIOS password.
- Encrypt the data on the hard drive.
- Use a strong logon password to the operating system.
- Back up everything on the laptop and store the backup in a safe place.
Subscribe
0 Comments
Newest