312-50 : CEH Certified Ethical Hacker (312-50v9) : Part 15
-
Which of the following is the successor of SSL?
- TLS
- RSA
- GRE
- IPSec
Explanation:
Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), both of which are frequently referred to as ‘SSL’, are cryptographic protocols that provide communications security over a computer network. -
You are attempting to man-in-the-middle a session. Which protocol will allow you to guess a sequence number?
- TCP
- UPD
- ICMP
- UPX
Explanation:
At the establishment of a TCP session the client starts by sending a SYN-packet (SYN=synchronize) with a sequence number. To hijack a session it is required to send a packet with a right seq-number, otherwise they are dropped. -
Your team has won a contract to infiltrate an organization. The company wants to have the attack be as realistic as possible; therefore, they did not provide any information besides the company name.
What should be the first step in security testing the client?
- Reconnaissance
- Enumeration
- Scanning
- Escalation
Explanation:
Phases of hacking
Phase 1—Reconnaissance
Phase 2—Scanning
Phase 3—Gaining Access
Phase 4—Maintaining Access
Phase 5—Covering TracksPhase 1: Passive and Active Reconnaissance
– Passive reconnaissance involves gathering information regarding a potential target without the targeted individual’s or company’s knowledge.
– Active reconnaissance involves probing the network to discover individual hosts, IP addresses, and services on the network. -
Which regulation defines security and privacy controls for Federal information systems and organizations?
- NIST-800-53
- PCI-DSS
- EU Safe Harbor
- HIPAA
Explanation:
NIST Special Publication 800-53, “Security and Privacy Controls for Federal Information Systems and Organizations,” provides a catalog of security controls for all U.S. federal information systems except those related to national security. -
How does the Address Resolution Protocol (ARP) work?
- It sends a request packet to all the network elements, asking for the MAC address from a specific IP.
- It sends a reply packet to all the network elements, asking for the MAC address from a specific IP.
- It sends a reply packet for a specific IP, asking for the MAC address.
- It sends a request packet to all the network elements, asking for the domain name from a specific IP.
Explanation:
When an incoming packet destined for a host machine on a particular local area network arrives at a gateway, the gateway asks the ARP program to find a physical host or MAC address that matches the IP address. The ARP program looks in the ARP cache and, if it finds the address, provides it so that the packet can be converted to the right packet length and format and sent to the machine. If no entry is found for the IP address, ARP broadcasts a request packet in a special format to all the machines on the LAN to see if one machine knows that it has that IP address associated with it. A machine that recognizes the IP address as its own returns a reply so indicating. ARP updates the ARP cache for future reference and then sends the packet to the MAC address that replied. -
You are performing information gathering for an important penetration test. You have found pdf, doc, and images in your objective. You decide to extract metadata from these files and analyze it.
What tool will help you with the task?
- Metagoofil
- Armitage
- Dimitry
- cdpsnarf
Explanation:
Metagoofil is an information gathering tool designed for extracting metadata of public documents (pdf,doc,xls,ppt,docx,pptx,xlsx) belonging to a target company.Metagoofil will perform a search in Google to identify and download the documents to local disk and then will extract the metadata with different libraries like Hachoir, PdfMiner? and others. With the results it will generate a report with usernames, software versions and servers or machine names that will help Penetration testers in the information gathering phase.
-
When you are collecting information to perform a data analysis, Google commands are very useful to find sensitive information and files. These files may contain information about passwords, system functions, or documentation.
What command will help you to search files using Google as a search engine?
- site: target.com filetype:xls username password email
- inurl: target.com filename:xls username password email
- domain: target.com archive:xls username password email
- site: target.com file:xls username password email
Explanation:
If you include site: in your query, Google will restrict your search results to the site or domain you specify.
If you include filetype:suffix in your query, Google will restrict the results to pages whose names end in suffix. For example, [ web page evaluation checklist filetype:pdf ] will return Adobe Acrobat pdf files that match the terms “web,” “page,” “evaluation,” and “checklist.” -
What is a “Collision attack” in cryptography?
- Collision attacks try to find two inputs producing the same hash.
- Collision attacks try to break the hash into two parts, with the same bytes in each part to get the private key.
- Collision attacks try to get the public key.
- Collision attacks try to break the hash into three parts to get the plaintext value.
Explanation:
A Collision Attack is an attempt to find two input strings of a hash function that produce the same hash result. -
You are tasked to perform a penetration test. While you are performing information gathering, you find an employee list in Google. You find the receptionist’s email, and you send her an email changing the source email to her boss’s email( boss@company ). In this email, you ask for a pdf with information. She reads your email and sends back a pdf with links. You exchange the pdf links with your malicious links (these links contain malware) and send back the modified pdf, saying that the links don’t work. She reads your email, opens the links, and her machine gets infected. You now have access to the company network.
What testing method did you use?
- Social engineering
- Tailgating
- Piggybacking
- Eavesdropping
Explanation:
Social engineering, in the context of information security, refers to psychological manipulation of people into performing actions or divulging confidential information. A type of confidence trick for the purpose of information gathering, fraud, or system access, it differs from a traditional “con” in that it is often one of many steps in a more complex fraud scheme.Incorrect Answers:
B: Using tailgaiting an attacker, seeking entry to a restricted area secured by unattended, electronic access control, e.g. by RFID card, simply walks in behind a person who has legitimate access. -
When you are getting information about a web server, it is very important to know the HTTP Methods (GET, POST, HEAD, PUT, DELETE, TRACE) that are available because there are two critical methods (PUT and DELETE). PUT can upload a file to the server and DELETE can delete a file from the server. You can detect all these methods (GET, POST, HEAD, PUT, DELETE, TRACE) using NMAP script engine.
What nmap script will help you with this task?
- http-methods
- http enum
- http-headers
- http-git
Explanation:
You can check HTTP method vulnerability using NMAP.
Example: #nmap –script=http-methods.nse 192.168.0.25 -
When you are testing a web application, it is very useful to employ a proxy tool to save every request and response. You can manually test every request and analyze the response to find vulnerabilities. You can test parameter and headers manually to get more precise results than if using web vulnerability scanners.
What proxy tool will help you find web vulnerabilities?
- Burpsuite
- Maskgen
- Dimitry
- Proxychains
Explanation:
Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities. -
You are a Network Security Officer. You have two machines. The first machine (192.168.0.99) has snort installed, and the second machine (192.168.0.150) has kiwi syslog installed. You perform a syn scan in your network, and you notice that kiwi syslog is not receiving the alert message from snort. You decide to run wireshark in the snort machine to check if the messages are going to the kiwi syslog machine.
What wireshark filter will show the connections from the snort machine to kiwi syslog machine?
- tcp.dstport==514 && ip.dst==192.168.0.150
- tcp.srcport==514 && ip.src==192.168.0.99
- tcp.dstport==514 && ip.dst==192.168.0.0/16
- tcp.srcport==514 && ip.src==192.168.150
Explanation:
We need to configure destination port at destination ip. The destination ip is 192.168.0.150, where the kiwi syslog is installed. -
This asymmetry cipher is based on factoring the product of two large prime numbers.
What cipher is described above?
- RSA
- SHA
- RC5
- MD5
Explanation:
RSA is based on the practical difficulty of factoring the product of two large prime numbers, the factoring problem.Note: A user of RSA creates and then publishes a public key based on two large prime numbers, along with an auxiliary value. The prime numbers must be kept secret. Anyone can use the public key to encrypt a message, but with currently published methods, if the public key is large enough, only someone with knowledge of the prime numbers can feasibly decode the message.
-
Which of the following parameters describe LM Hash (see exhibit):
Exhibit:
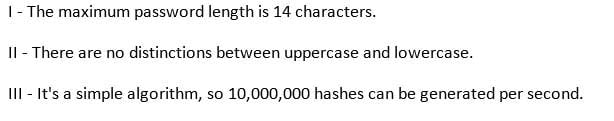
312-50 Part 15 Q14 014 - I, II, and III
- I
- II
- I and II
Explanation:
The LM hash is computed as follows:
1. The user’s password is restricted to a maximum of fourteen characters.
2. The user’s password is converted to uppercase.
Etc.
14 character Windows passwords, which are stored with LM Hash, can be cracked in five seconds. -
What is the process of logging, recording, and resolving events that take place in an organization?
- Incident Management Process
- Security Policy
- Internal Procedure
- Metrics
Explanation:
The activities within the incident management process include:
– Incident detection and recording
– Classification and initial support
– Investigation and analysis
– Resolution and record
– Incident closure
– Incident ownership, monitoring, tracking and communication
– Establish incident framework management
– Evaluation of incident framework management -
The Open Web Application Security Project (OWASP) is the worldwide not-for-profit charitable organization focused on improving the security of software. What item is the primary concern on OWASP’s Top Ten Project Most Critical Web Application Security Risks?
- Injection
- Cross Site Scripting
- Cross Site Request Forgery
- Path disclosure
Explanation:
The top item of the OWASP 2013 OWASP’s Top Ten Project Most Critical Web Application Security Risks is injection.
Injection flaws, such as SQL, OS, and LDAP injection occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization. -
You are performing a penetration test. You achieved access via a buffer overflow exploit and you proceed to find interesting data, such as files with usernames and passwords. You find a hidden folder that has the administrator’s bank account password and login information for the administrator’s bitcoin account.
What should you do?
- Report immediately to the administrator
- Do not report it and continue the penetration test.
- Transfer money from the administrator’s account to another account.
- Do not transfer the money but steal the bitcoins.
-
Which of the following describes the characteristics of a Boot Sector Virus?
- Moves the MBR to another location on the hard disk and copies itself to the original location of the MBR
- Moves the MBR to another location on the RAM and copies itself to the original location of the MBR
- Modifies directory table entries so that directory entries point to the virus code instead of the actual program
- Overwrites the original MBR and only executes the new virus code
Explanation:
A boot sector virus is a computer virus that infects a storage device’s master boot record (MBR). The virus moves the boot sector to another location on the hard drive. -
You have several plain-text firewall logs that you must review to evaluate network traffic. You know that in order to do fast, efficient searches of the logs you must use regular expressions.
Which command-line utility are you most likely to use?
- Grep
- Notepad
- MS Excel
- Relational Database
Explanation:
grep is a command-line utility for searching plain-text data sets for lines matching a regular expression. -
You’ve just been hired to perform a pen test on an organization that has been subjected to a large-scale attack. The CIO is concerned with mitigating threats and vulnerabilities to totally eliminate risk.
What is one of the first things you should do when given the job?
- Explain to the CIO that you cannot eliminate all risk, but you will be able to reduce risk to acceptable levels.
- Interview all employees in the company to rule out possible insider threats.
- Establish attribution to suspected attackers.
- Start the wireshark application to start sniffing network traffic.
Explanation:
The goals of penetration tests are:
– Determine feasibility of a particular set of attack vectors
– Identify high-risk vulnerabilities from a combination of lower-risk vulnerabilities exploited in a particular sequence
– Identify vulnerabilities that may be difficult or impossible to detect with automated network or application vulnerability scanning software
– Assess the magnitude of potential business and operational impacts of successful attacks
– Test the ability of network defenders to detect and respond to attacks
– Provide evidence to support increased investments in security personnel and technology