312-50 : CEH Certified Ethical Hacker (312-50v9) : Part 26
-
Which type of cryptography does SSL, IKE and PGP belongs to?
- Secret Key
- Hash Algorithm
- Digest
- Public Key
-
A recent security audit revealed that there were indeed several occasions that the company’s network was breached. After investigating, you discover that your IDS is not configured properly and therefore is unable to trigger alarms when needed. What type of alert is the IDS giving?
- True Positive
- False Negative
- False Positive
- False Positive
-
What are two things that are possible when scanning UDP ports? (Choose two.)
- A reset will be returned
- An ICMP message will be returned
- The four-way handshake will not be completed
- An RFC 1294 message will be returned
- Nothing
-
What does a type 3 code 13 represent? (Choose two.)
- Echo request
- Destination unreachable
- Network unreachable
- Administratively prohibited
- Port unreachable
- Time exceeded
-
Destination unreachable administratively prohibited messages can inform the hacker to what?
- That a circuit level proxy has been installed and is filtering traffic
- That his/her scans are being blocked by a honeypot or jail
- That the packets are being malformed by the scanning software
- That a router or other packet-filtering device is blocking traffic
- That the network is functioning normally
-
Which of the following Nmap commands would be used to perform a stack fingerprinting?
- Nmap -O -p80 <host(s.>
- Nmap -hU -Q<host(s.>
- Nmap -sT -p <host(s.>
- Nmap -u -o -w2 <host>
- Nmap -sS -0p targe
-
(Note: the student is being tested on concepts learnt during passive OS fingerprinting, basic TCP/IP connection concepts and the ability to read packet signatures from a sniff dump.). Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal. If you were the penetration tester, why would you find this abnormal?
What is odd about this attack? Choose the best answer.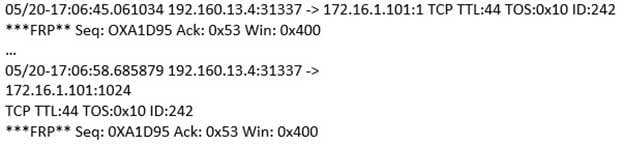
312-50 Part 26 Q07 026 - This is not a spoofed packet as the IP stack has increasing numbers for the three flags.
- This is back orifice activity as the scan comes from port 31337.
- The attacker wants to avoid creating a sub-carries connection that is not normally valid.
- These packets were crafted by a tool, they were not created by a standard IP stack.
-
Which type of Nmap scan is the most reliable, but also the most visible, and likely to be picked up by and IDS?
- SYN scan
- ACK scan
- RST scan
- Connect scan
- FIN scan
-
Name two software tools used for OS guessing? (Choose two.)
- Nmap
- Snadboy
- Queso
- UserInfo
- NetBus
-
Sandra is the security administrator of XYZ.com. One day she notices that the XYZ.com Oracle database server has been compromised and customer information along with financial data has been stolen. The financial loss will be estimated in millions of dollars if the database gets into the hands of competitors. Sandra wants to report this crime to the law enforcement agencies immediately. Which organization coordinates computer crime investigations throughout the United States?
- NDCA
- NICP
- CIRP
- NPC
- CIA
-
While reviewing the result of scanning run against a target network you come across the following:
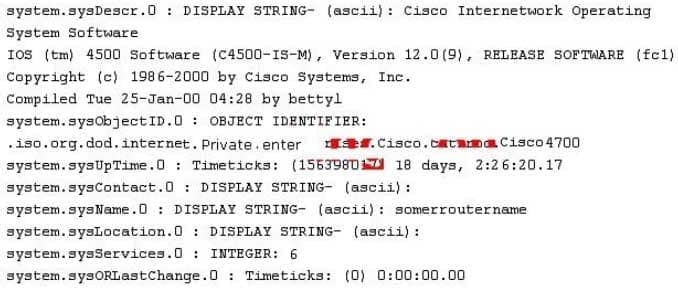
312-50 Part 26 Q11 027 Which among the following can be used to get this output?
- A Bo2k system query.
- nmap protocol scan
- A sniffer
- An SNMP walk
-
You are manually conducting Idle Scanning using Hping2. During your scanning you notice that almost every query increments the IPID regardless of the port being queried. One or two of the queries cause the IPID to increment by more than one value. Why do you think this occurs?
- The zombie you are using is not truly idle.
- A stateful inspection firewall is resetting your queries.
- Hping2 cannot be used for idle scanning.
- These ports are actually open on the target system.
-
While performing ping scans into a target network you get a frantic call from the organization’s security team. They report that they are under a denial of service attack. When you stop your scan, the smurf attack event stops showing up on the organization’s IDS monitor.
How can you modify your scan to prevent triggering this event in the IDS?
- Scan more slowly.
- Do not scan the broadcast IP.
- Spoof the source IP address.
- Only scan the Windows systems.
-
Neil notices that a single address is generating traffic from its port 500 to port 500 of several other machines on the network. This scan is eating up most of the network bandwidth and Neil is concerned. As a security professional, what would you infer from this scan?
- It is a network fault and the originating machine is in a network loop
- It is a worm that is malfunctioning or hardcoded to scan on port 500
- The attacker is trying to detect machines on the network which have SSL enabled
- The attacker is trying to determine the type of VPN implementation and checking for IPSec
-
A distributed port scan operates by:
- Blocking access to the scanning clients by the targeted host
- Using denial-of-service software against a range of TCP ports
- Blocking access to the targeted host by each of the distributed scanning clients
- Having multiple computers each scan a small number of ports, then correlating the results
-
An nmap command that includes the host specification of 202.176.56-57.* will scan _______ number of hosts.
- 2
- 256
- 512
- Over 10, 000
-
A specific site received 91 ICMP_ECHO packets within 90 minutes from 47 different sites.
77 of the ICMP_ECHO packets had an ICMP ID:39612 and Seq:57072. 13 of the ICMP_ECHO packets had an ICMP ID:0 and Seq:0. What can you infer from this information?
- The packets were sent by a worm spoofing the IP addresses of 47 infected sites
- ICMP ID and Seq numbers were most likely set by a tool and not by the operating system
- All 77 packets came from the same LAN segment and hence had the same ICMP ID and Seq number
- 13 packets were from an external network and probably behind a NAT, as they had an ICMP ID 0 and Seq 0
-
Which of the following commands runs snort in packet logger mode?
- ./snort -dev -h ./log
- ./snort -dev -l ./log
- ./snort -dev -o ./log
- ./snort -dev -p ./log
-
You have initiated an active operating system fingerprinting attempt with nmap against a target system:

312-50 Part 26 Q19 028 What operating system is the target host running based on the open ports shown above?
- Windows XP
- Windows 98 SE
- Windows NT4 Server
- Windows 2000 Server
-
Study the log below and identify the scan type.
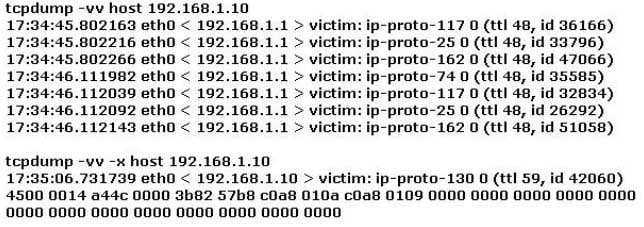
312-50 Part 26 Q20 029 - nmap -sR 192.168.1.10
- nmap -sS 192.168.1.10
- nmap -sV 192.168.1.10
- nmap -sO -T 192.168.1.10
Subscribe
0 Comments
Newest