312-50 : CEH Certified Ethical Hacker (312-50v9) : Part 30
-
While examining audit logs, you discover that people are able to telnet into the SMTP server on port 25. You would like to block this, though you do not see any evidence of an attack or other wrong doing. However, you are concerned about affecting the normal functionality of the email server. From the following options choose how best you can achieve this objective?
- Block port 25 at the firewall.
- Shut off the SMTP service on the server.
- Force all connections to use a username and password.
- Switch from Windows Exchange to UNIX Sendmail.
- None of the above.
-
Windows LAN Manager (LM) hashes are known to be weak.
Which of the following are known weaknesses of LM? (Choose three.)
- Converts passwords to uppercase.
- Hashes are sent in clear text over the network.
- Makes use of only 32-bit encryption.
- Effective length is 7 characters.
-
You have retrieved the raw hash values from a Windows 2000 Domain Controller. Using social engineering, you come to know that they are enforcing strong passwords. You understand that all users are required to use passwords that are at least 8 characters in length. All passwords must also use 3 of the 4 following categories: lower case letters, capital letters, numbers and special characters. With your existing knowledge of users, likely user account names and the possibility that they will choose the easiest passwords possible, what would be the fastest type of password cracking attack you can run against these hash values and still get results?
- Online Attack
- Dictionary Attack
- Brute Force Attack
- Hybrid Attack
-
An attacker runs netcat tool to transfer a secret file between two hosts.

312-50 Part 30 Q04 037 He is worried about information being sniffed on the network.
How would the attacker use netcat to encrypt the information before transmitting onto the wire?- Machine A: netcat -l -p -s password 1234 < testfile
Machine B: netcat <machine A IP> 1234 - Machine A: netcat -l -e magickey -p 1234 < testfile
Machine B: netcat <machine A IP> 1234 - Machine A: netcat -l -p 1234 < testfile -pw password
Machine B: netcat <machine A IP> 1234 -pw password - Use cryptcat instead of netcat
- Machine A: netcat -l -p -s password 1234 < testfile
-
What is GINA?
- Gateway Interface Network Application
- GUI Installed Network Application CLASS
- Global Internet National Authority (G-USA)
- Graphical Identification and Authentication DLL
-
Fingerprinting an Operating System helps a cracker because:
- It defines exactly what software you have installed
- It opens a security-delayed window based on the port being scanned
- It doesn’t depend on the patches that have been applied to fix existing security holes
- It informs the cracker of which vulnerabilities he may be able to exploit on your system
-
In the context of Windows Security, what is a ‘null’ user?
- A user that has no skills
- An account that has been suspended by the admin
- A pseudo account that has no username and password
- A pseudo account that was created for security administration purpose
-
What does the following command in netcat do?
nc -l -u -p55555 < /etc/passwd
- logs the incoming connections to /etc/passwd file
- loads the /etc/passwd file to the UDP port 55555
- grabs the /etc/passwd file when connected to UDP port 55555
- deletes the /etc/passwd file when connected to the UDP port 55555
-
What hacking attack is challenge/response authentication used to prevent?
- Replay attacks
- Scanning attacks
- Session hijacking attacks
- Password cracking attacks
-
In this attack, a victim receives an e-mail claiming from PayPal stating that their account has been disabled and confirmation is required before activation. The attackers then scam to collect not one but two credit card numbers, ATM PIN number and other personal details. Ignorant users usually fall prey to this scam.
Which of the following statement is incorrect related to this attack?
- Do not reply to email messages or popup ads asking for personal or financial information
- Do not trust telephone numbers in e-mails or popup ads
- Review credit card and bank account statements regularly
- Antivirus, anti-spyware, and firewall software can very easily detect these type of attacks
- Do not send credit card numbers, and personal or financial information via e-mail
-
Bob is going to perform an active session hijack against Brownies Inc. He has found a target that allows session oriented connections (Telnet) and performs the sequence prediction on the target operating system. He manages to find an active session due to the high level of traffic on the network. What is Bob supposed to do next?
- Take over the session
- Reverse sequence prediction
- Guess the sequence numbers
- Take one of the parties offline
-
ViruXine.W32 virus hides their presence by changing the underlying executable code.
This Virus code mutates while keeping the original algorithm intact, the code changes itself each time it runs, but the function of the code (its semantics) will not change at all.
312-50 Part 30 Q12 038 Here is a section of the Virus code:
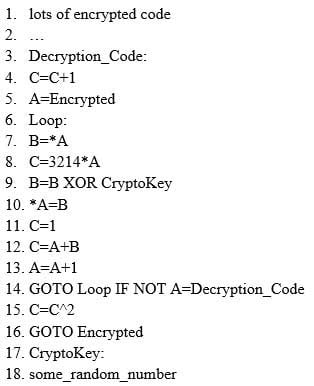
312-50 Part 30 Q12 039 What is this technique called?
- Polymorphic Virus
- Metamorphic Virus
- Dravidic Virus
- Stealth Virus
-
Identify the correct terminology that defines the above statement.

312-50 Part 30 Q13 040 - Vulnerability Scanning
- Penetration Testing
- Security Policy Implementation
- Designing Network Security
-
Nathan is testing some of his network devices. Nathan is using Macof to try and flood the ARP cache of these switches.
If these switches’ ARP cache is successfully flooded, what will be the result?
- The switches will drop into hub mode if the ARP cache is successfully flooded.
- If the ARP cache is flooded, the switches will drop into pix mode making it less susceptible to attacks.
- Depending on the switch manufacturer, the device will either delete every entry in its ARP cache or reroute packets to the nearest switch.
- The switches will route all traffic to the broadcast address created collisions.
-
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c

312-50 Part 30 Q15 041 What is the hexadecimal value of NOP instruction?
- 0x60
- 0x80
- 0x70
- 0x90
-
This TCP flag instructs the sending system to transmit all buffered data immediately.
- SYN
- RST
- PSH
- URG
- FIN
-
The network administrator at Spears Technology, Inc has configured the default gateway Cisco router’s access-list as below:
You are hired to conduct security testing on their network.
You successfully brute-force the SNMP community string using a SNMP crack tool.
The access-list configured at the router prevents you from establishing a successful connection.You want to retrieve the Cisco configuration from the router. How would you proceed?
- Use the Cisco’s TFTP default password to connect and download the configuration file
- Run a network sniffer and capture the returned traffic with the configuration file from the router
- Run Generic Routing Encapsulation (GRE) tunneling protocol from your computer to the router masking your IP address
- Send a customized SNMP set request with a spoofed source IP address in the range -192.168.1.0
-
You work for Acme Corporation as Sales Manager. The company has tight network security restrictions. You are trying to steal data from the company’s Sales database (Sales.xls) and transfer them to your home computer. Your company filters and monitors traffic that leaves from the internal network to the Internet. How will you achieve this without raising suspicion?
- Encrypt the Sales.xls using PGP and e-mail it to your personal gmail account
- Package the Sales.xls using Trojan wrappers and telnet them back your home computer
- You can conceal the Sales.xls database in another file like photo.jpg or other files and send it out in an innocent looking email or file transfer using Steganography techniques
- Change the extension of Sales.xls to sales.txt and upload them as attachment to your hotmail account
-
Study the snort rule given below and interpret the rule. alert tcp any any –> 192.168.1.0/24 111
(content:”|00 01 86 a5|”; msG. “mountd access”;)
- An alert is generated when a TCP packet is generated from any IP on the 192.168.1.0 subnet and destined to any IP on port 111
- An alert is generated when any packet other than a TCP packet is seen on the network and destined for the 192.168.1.0 subnet
- An alert is generated when a TCP packet is originated from port 111 of any IP address to the 192.168.1.0 subnet
- An alert is generated when a TCP packet originating from any IP address is seen on the network and destined for any IP address on the 192.168.1.0 subnet on port 111
-
What port number is used by LDAP protocol?
- 110
- 389
- 464
- 445
Subscribe
0 Comments
Newest