312-50 : CEH Certified Ethical Hacker (312-50v9) : Part 31
-
Fred is the network administrator for his company. Fred is testing an internal switch.
From an external IP address, Fred wants to try and trick this switch into thinking it already has established a session with his computer. How can Fred accomplish this?
- Fred can accomplish this by sending an IP packet with the RST/SIN bit and the source address of his computer.
- He can send an IP packet with the SYN bit and the source address of his computer.
- Fred can send an IP packet with the ACK bit set to zero and the source address of the switch.
- Fred can send an IP packet to the switch with the ACK bit and the source address of his machine.
-
Within the context of Computer Security, which of the following statements describes Social Engineering best?
- Social Engineering is the act of publicly disclosing information
- Social Engineering is the means put in place by human resource to perform time accounting
- Social Engineering is the act of getting needed information from a person rather than breaking into a system
- Social Engineering is a training program within sociology studies
-
In Trojan terminology, what is a covert channel?

312-50 Part 31 Q03 042 - A channel that transfers information within a computer system or network in a way that violates the security policy
- A legitimate communication path within a computer system or network for transfer of data
- It is a kernel operation that hides boot processes and services to mask detection
- It is Reverse tunneling technique that uses HTTPS protocol instead of HTTP protocol to establish connections
-
When a normal TCP connection starts, a destination host receives a SYN (synchronize/start) packet from a source host and sends back a SYN/ACK (synchronize acknowledge). The destination host must then hear an ACK (acknowledge) of the SYN/ACK before the connection is established. This is referred to as the “TCP three-way handshake.” While waiting for the ACK to the SYN ACK, a connection queue of finite size on the destination host keeps track of connections waiting to be completed. This queue typically empties quickly since the ACK is expected to arrive a few milliseconds after the SYN ACK.
How would an attacker exploit this design by launching TCP SYN attack?
- Attacker generates TCP SYN packets with random destination addresses towards a victim host
- Attacker floods TCP SYN packets with random source addresses towards a victim host
- Attacker generates TCP ACK packets with random source addresses towards a victim host
- Attacker generates TCP RST packets with random source addresses towards a victim host
-
Yancey is a network security administrator for a large electric company. This company provides power for over 100, 000 people in Las Vegas. Yancey has worked for his company for over 15 years and has become very successful. One day, Yancey comes in to work and finds out that the company will be downsizing and he will be out of a job in two weeks. Yancey is very angry and decides to place logic bombs, viruses, Trojans, and backdoors all over the network to take down the company once he has left. Yancey does not care if his actions land him in jail for 30 or more years, he just wants the company to pay for what they are doing to him.
What would Yancey be considered?
- Yancey would be considered a Suicide Hacker
- Since he does not care about going to jail, he would be considered a Black Hat
- Because Yancey works for the company currently; he would be a White Hat
- Yancey is a Hacktivist Hacker since he is standing up to a company that is downsizing
-
You receive an e-mail like the one shown below. When you click on the link contained in the mail, you are redirected to a website seeking you to download free Anti-Virus software.
Dear valued customers,
We are pleased to announce the newest version of Antivirus 2010 for Windows which will probe you with total security against the latest spyware, malware, viruses, Trojans and other online threats. Simply visit the link below and enter your antivirus code: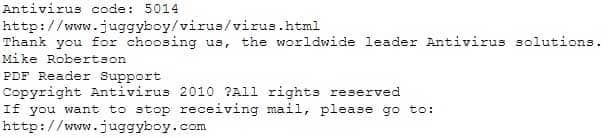
312-50 Part 31 Q06 043 or you may contact us at the following address:
Media Internet Consultants, Edif. Neptuno, Planta
Baja, Ave. Ricardo J. Alfaro, Tumba Muerto, n/a PanamaHow will you determine if this is Real Anti-Virus or Fake Anti-Virus website?
- Look at the website design, if it looks professional then it is a Real Anti-Virus website
- Connect to the site using SSL, if you are successful then the website is genuine
- Search using the URL and Anti-Virus product name into Google and lookout for suspicious warnings against this site
- Download and install Anti-Virus software from this suspicious looking site, your Windows 7 will prompt you and stop the installation if the downloaded file is a malware
- Download and install Anti-Virus software from this suspicious looking site, your Windows 7 will prompt you and stop the installation if the downloaded file is a malware
-
Every company needs a formal written document which spells out to employees precisely what they are allowed to use the company’s systems for, what is prohibited, and what will happen to them if they break the rules. Two printed copies of the policy should be given to every employee as soon as possible after they join the organization. The employee should be asked to sign one copy, which should be safely filed by the company. No one should be allowed to use the company’s computer systems until they have signed the policy in acceptance of its terms.
What is this document called?
- Information Audit Policy (IAP)
- Information Security Policy (ISP)
- Penetration Testing Policy (PTP)
- Company Compliance Policy (CCP)
-
Take a look at the following attack on a Web Server using obstructed URL:
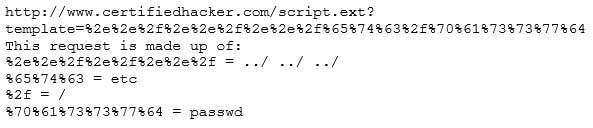
312-50 Part 31 Q08 044 How would you protect from these attacks?
- Configure the Web Server to deny requests involving “hex encoded” characters
- Create rules in IDS to alert on strange Unicode requests
- Use SSL authentication on Web Servers
- Enable Active Scripts Detection at the firewall and routers
-
Which type of sniffing technique is generally referred as MiTM attack?
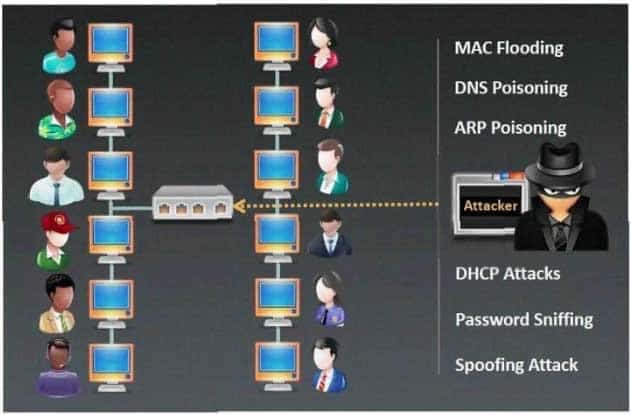
312-50 Part 31 Q09 045 - Password Sniffing
- ARP Poisoning
- Mac Flooding
- DHCP Sniffing
-
Switches maintain a CAM Table that maps individual MAC addresses on the network to physical ports on the switch.
312-50 Part 31 Q10 046 In MAC flooding attack, a switch is fed with many Ethernet frames, each containing different source MAC addresses, by the attacker. Switches have a limited memory for mapping various MAC addresses to physical ports. What happens when the CAM table becomes full?
- Switch then acts as hub by broadcasting packets to all machines on the network
- The CAM overflow table will cause the switch to crash causing Denial of Service
- The switch replaces outgoing frame switch factory default MAC address of FF:FF:FF:FF:FF:FF
- Every packet is dropped and the switch sends out SNMP alerts to the IDS port
-
You went to great lengths to install all the necessary technologies to prevent hacking attacks, such as expensive firewalls, antivirus software, anti-spam systems and intrusion detection/prevention tools in your company’s network. You have configured the most secure policies and tightened every device on your network. You are confident that hackers will never be able to gain access to your network with complex security system in place.
Your peer, Peter Smith who works at the same department disagrees with you.
He says even the best network security technologies cannot prevent hackers gaining access to the network because of presence of “weakest link” in the security chain.
What is Peter Smith talking about?
- Untrained staff or ignorant computer users who inadvertently become the weakest link in your security chain
- “zero-day” exploits are the weakest link in the security chain since the IDS will not be able to detect these attacks
- “Polymorphic viruses” are the weakest link in the security chain since the Anti-Virus scanners will not be able to detect these attacks
- Continuous Spam e-mails cannot be blocked by your security system since spammers use different techniques to bypass the filters in your gateway
-
How does a denial-of-service attack work?
- A hacker prevents a legitimate user (or group of users) from accessing a service
- A hacker uses every character, word, or letter he or she can think of to defeat authentication
- A hacker tries to decipher a password by using a system, which subsequently crashes the network
- A hacker attempts to imitate a legitimate user by confusing a computer or even another person
-
You are trying to break into a highly classified top-secret mainframe computer with highest security system in place at Merclyn Barley Bank located in Los Angeles.
You know that conventional hacking doesn’t work in this case, because organizations such as banks are generally tight and secure when it comes to protecting their systems.
In other words, you are trying to penetrate an otherwise impenetrable system.
How would you proceed?
- Look for “zero-day” exploits at various underground hacker websites in Russia and China and buy the necessary exploits from these hackers and target the bank’s network
- Try to hang around the local pubs or restaurants near the bank, get talking to a poorly-paid or disgruntled employee, and offer them money if they’ll abuse their access privileges by providing you with sensitive information
- Launch DDOS attacks against Merclyn Barley Bank’s routers and firewall systems using 100, 000 or more “zombies” and “bots”
- Try to conduct Man-in-the-Middle (MiTM) attack and divert the network traffic going to the Merclyn Barley Bank’s Webserver to that of your machine using DNS Cache Poisoning techniques
-
This is an attack that takes advantage of a web site vulnerability in which the site displays content that includes un-sanitized user-provided data.

312-50 Part 31 Q14 047 What is this attack?
- Cross-site-scripting attack
- SQL Injection
- URL Traversal attack
- Buffer Overflow attack
Subscribe
0 Comments
Newest