312-38 : Certified Network Defender : Part 22
-
The SNMP contains various commands that reduce the burden on the network administrators. Which of the following commands is used by SNMP agents to notify SNMP managers about an event occurring in the network?
- INFORM
- RESPONSE
- TRAPS
- SET
-
As a network administrator, you have implemented WPA2 encryption in your corporate wireless network. The WPA2’s __________ integrity check mechanism provides security against a replay attack.
- CBC-MAC
- CRC-MAC
- CBC-32
- CRC-32
-
Paul is a network security technician working on a contract for a laptop manufacturing company in Chicago. He has focused primarily on securing network devices, firewalls, and traffic traversing in and out of the network. He just finished setting up a server a gateway between the internal private network and the outside public network. This server will act as a proxy, limited amount of services, and will filter packets. What is this type of server called?
- Session layer firewall.
- SOCKS host.
- Bastion host.
- Edge transport server.
-
Your company is planning to use an uninterruptible power supply (UPS) to avoid damage from power fluctuations. As a network administrator, you need to suggest an appropriate UPS solution suitable for specific resources or conditions. Match the type of UPS with the use and advantage:
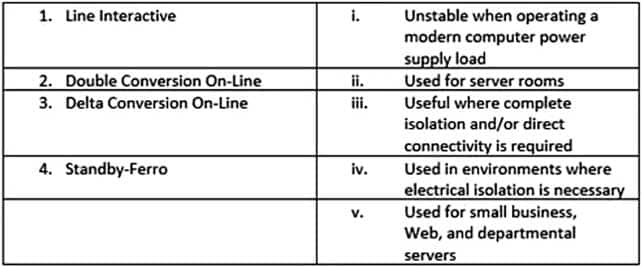
312-38 Part 22 Q04 030 - 1-i,2-iv,3-ii,4-v
- 1-v,2-iii,3-i,4-ii
- 1-ii,2-iv,3-iii,4-i
- 1-iii,2-iv,3-v,4-iv
-
John has successfully remediated the vulnerability of an internal application that could have caused a threat to the network. He is scanning the application for the existence of a remediated vulnerability, this process is called a __________ and it has to adhere to the __________.
- Mitigation, Security policies
- Verification, Security Policies
- Vulnerability scanning, Risk Analysis
- Risk analysis, Risk matrix
-
Which filter to locate unusual ICMP request an Analyst can use in order to detect a ICMP probes from the attacker to a target OS looking for the response to perform ICMP based fingerprinting?
- (icmp.type==9 && ((!(icmp.code==9))
- (icmp.type==8 && ((!(icmp.code==8))
- (icmp.type==12) | | (icmp.type==15| |(icmp.type==17)
- (icmp.type==14) | | (icmp.type==15| |(icmp.type==17)
-
You are using Wireshark to monitor your network traffic and you see a lot of packages with the FIN, PUSH and URG flags activated; what can you infer about this behavior?
- The Layer 3 Controls are activated in the Switches
- The Spanning Tree Protocol is activated in the Switches
- One NIC is broadcasting erroneous traffic
- An attacker is running a XMAS scan against the network
-
The Circuit-level gateway firewall technology functions at which of the following OSI layer?
- Transport layer
- Data-link layer
- Session layer
- Network layer
-
Individuals in the organization using system resources in a way that violates acceptable usage policies indicates which of the following security incident(s):
- Unauthorized Access
- Improper Usage
- Denial-of-Service (DoS)
- Malicious Code
-
The GMT enterprise is working on their internet and web usage policies. GMT would like to control internet bandwidth consumption by employees. Which group of policies would this belong to?
- Enterprise Information Security Policy
- Network Services Specific Security Policy
- Issue Specific Security Policy
- System Specific Security Policy
-
Which of the following intrusion detection techniques observes the network for abnormal usage patterns by determining the performance parameters for regular activities and monitoring for actions beyond the normal parameters?
- Statistical anomaly detection
- Signature/Pattern matching
- None of these
- Stateful protocol analysis
-
An administrator wants to monitor and inspect large amounts of traffic and detect unauthorized attempts from inside the organization, with the help of an IDS. They are not able to recognize the exact location to deploy the IDS sensor. Can you help him spot the location where the IDS sensor should be placed?

312-38 Part 22 Q12 031 - Location 1
- Location 2
- Location 3
- Location 4
-
Steven’s company has recently grown from 5 employees to over 50. Every workstation has a public IP address and navigated to the Internet with little to no protection. Steven wants to use a firewall. He also wants IP addresses to be private addresses, to prevent public Internet devices direct access to them. What should Steven implement on the firewall to ensure this happens?
- Steven should use Open Shortest Path First (OSPF).
- Steven should enable Network Address Translation (NAT).
- Steven should use a Demilitarized Zone (DMZ).
- Steven should use IPsec.
-
Assume that you are a network administrator and the company has asked you to draft an Acceptable Use Policy (AUP) for employees. Under which category of an information security policy does AUP fall into?
- Incident Response Policy (IRP)
- Issue Specific Security Policy (ISSP)
- Enterprise Information Security Policy (EISP)
- System Specific Security Policy (SSSP)
-
During the recovery process, RTO and RPO should be the main parameters of your disaster recovery plan. What does RPO refer to?
- The encryption feature, acting as add-on security to the data
- The hot plugging technique used to replace computer components
- The duration required to restore the data
- The interval after which the data quality is lost
-
Ryan works as a network security engineer at an organization the recently suffered an attack. As a countermeasure, Ryan would like to obtain more information about the attacker and chooses to deploy a honeypot into the organizations production environment called Kojoney. Using this honeypot, he would like to emulate the network vulnerability that was attacked previously. Which type of honeypot is he trying to implement?
- High interaction honeypots
- Research honeypot
- Low interaction honeypots
- Pure honeypots
-
James is a network administrator working at a student loan company in Minnesota. This company processes over 20,000 student loans a year from colleges all over the state. Most communication between the company, schools, and lenders is carried out through emails. Much of the email communication used at his company contains sensitive information such as social security numbers. For this reason, James wants to utilize email encryption. Since a server-based PKI is not an option for him, he is looking for a low/no cost solution to encrypt emails. What should James use?
- James should utilize the free OTP software package.
- James can enforce mandatory HTTPS in the email clients to encrypt emails.
- James could use PGP as a free option for encrypting the company’s emails.
- James can use MD5 algorithm to encrypt all the emails.
-
David is working in a mid-sized IT company. Management asks him to suggest a framework that can be used effectively to align the IT goals to the business goals of the company. David suggests the _________ framework, as it provides a set of controls over IT and consolidates them to form a framework.
- COBIT
- ITIL
- ISO 27007
- RMIS
-
Identify the password cracking attempt involving precomputed hash values stored as plaintext and used to crack the password.
- Bruteforce
- Rainbow table
- Hybrid
- Dictionary
-
John, the network administrator and he wants to enable the NetFlow feature in Cisco routers to collect and monitor the IP network traffic passing through the router. Which command will John use to enable NetFlow on an interface?
-
Router IP route
-
Router(Config-if) # IP route cache flow -
Router# Netmon enable
-
Router# netflow enable
-
Subscribe
0 Comments
Newest