SY0-501 : CompTIA Security+ Certification : Part 22
-
Ann is the IS manager for several new systems in which the classifications of the systems’ data are being decided. She is trying to determine the sensitivity level of the data being processed. Which of the following people should she consult to determine the data classification?
- Steward
- Custodian
- User
- Owner
-
A systems administrator wants to generate a self-signed certificate for an internal website.
Which of the following steps should the systems administrator complete prior to installing the certificate on the server?
- Provide the private key to a public CA.
- Provide the public key to the internal CA.
- Provide the public key to a public CA.
- Provide the private key to the internal CA.
- Provide the public/private key pair to the internal CA
- Provide the public/private key pair to a public CA.
-
Which of the following controls allows a security guard to perform a post-incident review?
- Detective
- Preventive
- Corrective
- Deterrent
-
Attackers have been using revoked certificates for MITM attacks to steal credentials from employees of Company.com.
Which of the following options should Company.com implement to mitigate these attacks?
- Captive portal
- OCSP stapling
- Object identifiers
- Key escrow
- Extended validation certificate
-
After attempting to harden a web server, a security analyst needs to determine if an application remains vulnerable to SQL injection attacks.
Which of the following would BEST assist the analyst in making this determination?
- tracert
- Fuzzer
- nslookup
- Nmap
- netcat
-
A company is allowing a BYOD policy for its staff.
Which of the following is a best practice that can decrease the risk of users jailbreaking mobile devices?
- Install a corporately monitored mobile antivirus on the devices.
- Prevent the installation of applications from a third-party application store.
- Build a custom ROM that can prevent jailbreaking.
- Require applications to be digitally signed.
-
Which of the following describes the key difference between vishing and phishing attacks?
- Phishing is used by attackers to steal a person’s identity.
- Vishing attacks require some knowledge of the target of attack.
- Vishing attacks are accomplished using telephony services.
- Phishing is a category of social engineering attack.
-
Which of the following should a security analyst perform FIRST to determine the vulnerabilities of a legacy system?
- Passive scan
- Aggressive scan
- Credentialed scan
- Intrusive scan
-
Which of the following components of printers and MFDs are MOST likely to be used as vectors of compromise if they are improperly configured?
- Embedded web server
- Spooler
- Network interface
- LCD control panel
-
A hacker has a packet capture that contains:
SY0-501 Part 22 Q10 068 Which of the following tools will the hacker use against this type of capture?
- Password cracker
- Vulnerability scanner
- DLP scanner
- Fuzzer
-
A user downloads and installs an MP3 converter, and runs the application. Upon running the application, the antivirus detects a new port in a listening state. Which of the following has the user MOST likely executed?
- RAT
- Worm
- Ransomware
- Bot
-
An attacker exploited a vulnerability on a mail server using the code below.

SY0-501 Part 22 Q12 069 Which of the following BEST explains what the attacker is doing?
- The attacker is replacing a cookie.
- The attacker is stealing a document.
- The attacker is replacing a document.
- The attacker is deleting a cookie.
-
A security analyst is securing smartphones and laptops for a highly mobile workforce.
– Priorities include:
– Remote wipe capabilities
– Geolocation services
– Patch management and reporting
– Mandatory screen locks
– Ability to require passcodes and pins
– Ability to require encryption
Which of the following would BEST meet these requirements?
- Implementing MDM software
- Deploying relevant group policies to the devices
- Installing full device encryption
- Removing administrative rights to the devices
-
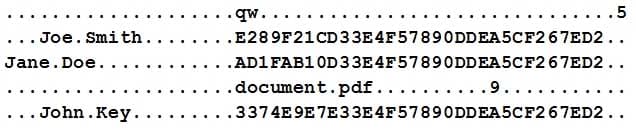
A technician receives a device with the following anomalies:
Frequent pop-up ads
Show response-time switching between active programs Unresponsive peripherals
The technician reviews the following log file entries:File Name Source MD5 Target MD5
Status
antivirus.exe F794F21CD33E4F57890DDEA5CF267ED2 F794F21CD33E4F57890DDEA5CF267ED2 Automatic iexplore.exe 7FAAF21CD33E4F57890DDEA5CF29CCEA AA87F21CD33E4F57890DDEAEE2197333 Automatic service.exe 77FF390CD33E4F57890DDEA5CF28881F 77FF390CD33E4F57890DDEA5CF28881F Manual USB.exe E289F21CD33E4F57890DDEA5CF28EDC0 E289F21CD33E4F57890DDEA5CF28EDC0 Stopped
Based on the above output, which of the following should be reviewed?
- The web application firewall
- The file integrity check
- The data execution prevention
- The removable media control
-
A CSIRT has completed restoration procedures related to a breach of sensitive data is creating documentation used to improve the organization’s security posture. The team has been specifically tasked to address logical controls in their suggestions. Which of the following would be MOST beneficial to include in lessons learned documentation? (Choose two.)
- A list of policies, which should be revised to provide better clarity to employees regarding acceptable use
- Recommendations relating to improved log correlation and alerting tools
- Data from the organization’s IDS/IPS tools, which show the timeline of the breach and the activities executed by the attacker
- A list of potential improvements to the organization’s NAC capabilities, which would improve AAA within the environment
- A summary of the activities performed during each phase of the incident response activity
- A list of topics that should be added to the organization’s security awareness training program based on weaknesses exploited during the attack
-
An organization plans to implement multifactor authentication techniques within the enterprise network architecture. Each authentication factor is expected to be a unique control.
Which of the following BEST describes the proper employment of multifactor authentication?
- Proximity card, fingerprint scanner, PIN
- Fingerprint scanner, voice recognition, proximity card
- Smart card, user PKI certificate, privileged user certificate
- Voice recognition, smart card, proximity card
-
Upon entering an incorrect password, the logon screen displays a message informing the user that the password does not match the username provided and is not the required length of 12 characters.
Which of the following secure coding techniques should a security analyst address with the application developers to follow security best practices?
- Input validation
- Error handling
- Obfuscation
- Data exposure
-
Which of the following is the BEST reason to run an untested application is a sandbox?
- To allow the application to take full advantage of the host system’s resources and storage
- To utilize the host systems antivirus and firewall applications instead of running it own protection
- To prevent the application from acquiring escalated privileges and accessing its host system
- To increase application processing speed so the host system can perform real-time logging
-
A security technician has been receiving alerts from several servers that indicate load balancers have had a significant increase in traffic. The technician initiates a system scan. The scan results illustrate that the disk space on several servers has reached capacity. The scan also indicates that incoming internet traffic to the servers has increased.
Which of the following is the MOST likely cause of the decreased disk space?
- Misconfigured devices
- Logs and events anomalies
- Authentication issues
- Unauthorized software
-
A security administrator is diagnosing a server where the CPU utilization is at 100% for 24 hours. The main culprit of CPU utilization is the antivirus program.
Which of the following issue could occur if left unresolved? (Choose two.)
- MITM attack
- DoS attack
- DLL injection
- Buffer overflow
- Resource exhaustion
Subscribe
0 Comments
Newest