SY0-501 : CompTIA Security+ Certification : Part 29
-
Which of the following is a compensating control that will BEST reduce the risk of weak passwords?
- Requiring the use of one-time tokens
- Increasing password history retention count
- Disabling user accounts after exceeding maximum attempts
- Setting expiration of user passwords to a shorter time
-
A consumer purchases an exploit from the dark web. The exploit targets the online shopping cart of a popular website, allowing the shopper to modify the price of an item at checkout. Which of the following BEST describes this type of user?
- Insider
- Script kiddie
- Competitor
- Hacktivist
- APT
-
HOTSPOT
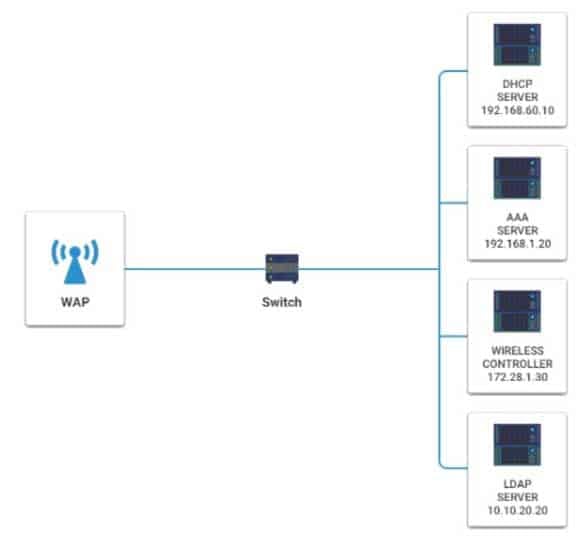
A newly purchased corporate WAP needs to be configured in the MOST secure manner possible.
INSTRUCTIONS
Please click on the below items on the network diagram and configure them accordingly:
– WAP
– DHCP Server
– AAA Server
– Wireless Controller
– LDAP ServerIf at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
SY0-501 Part 29 Q03 075 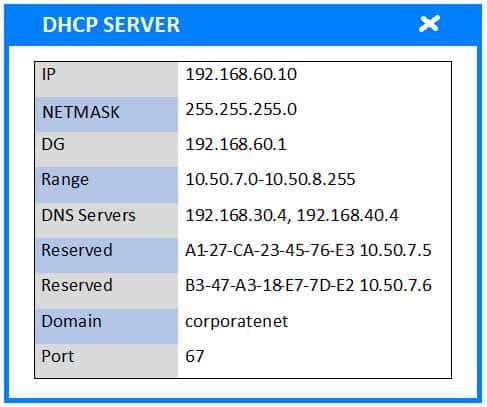
SY0-501 Part 29 Q03 076 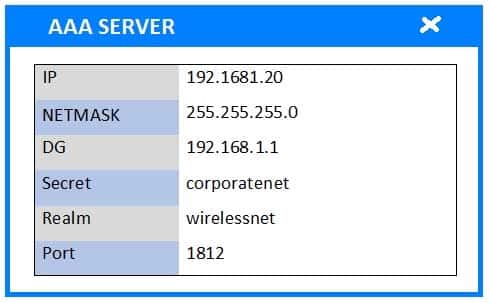
SY0-501 Part 29 Q03 077 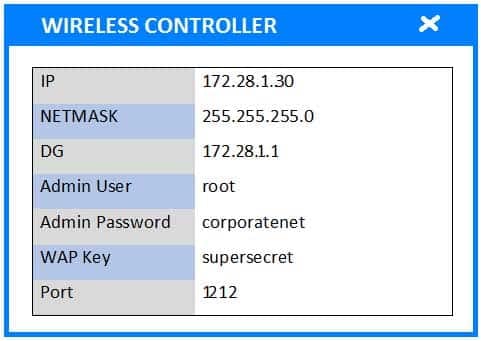
SY0-501 Part 29 Q03 078 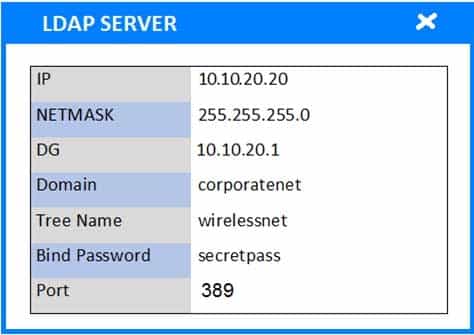
SY0-501 Part 29 Q03 079 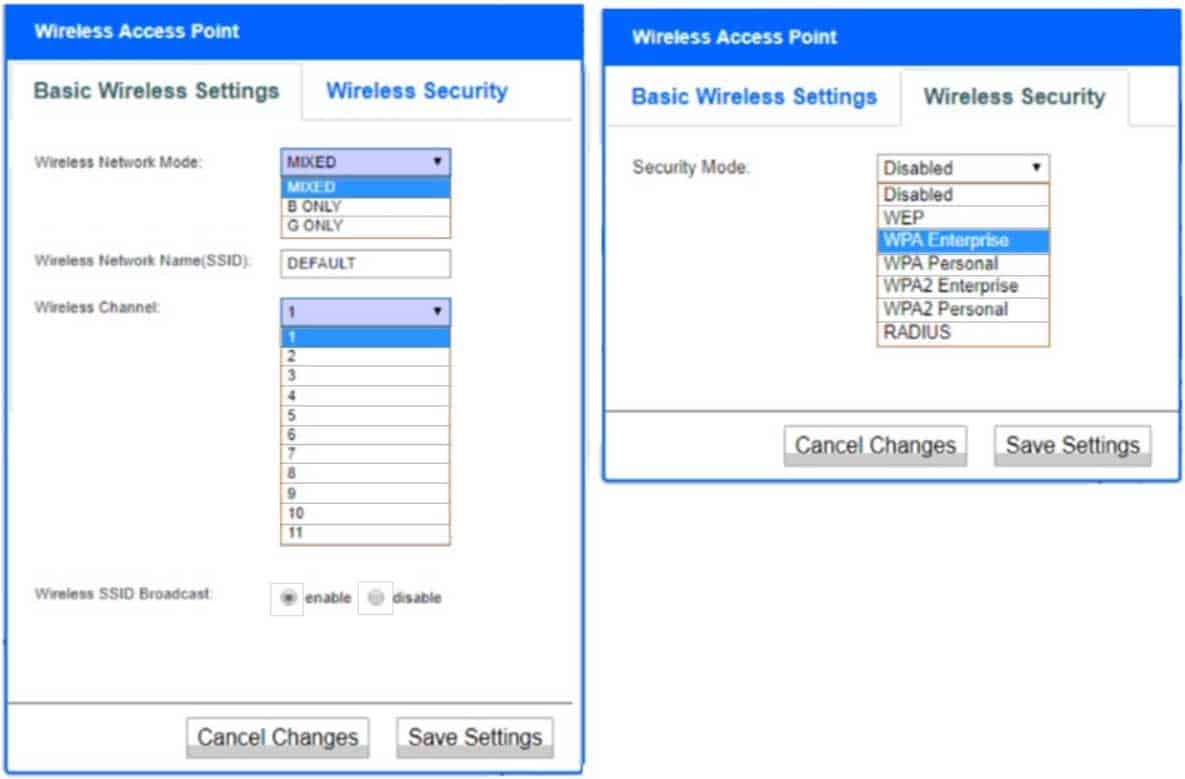
SY0-501 Part 29 Q03 080 Question 
SY0-501 Part 29 Q03 080 Answer -
DRAG DROP
A security auditor is reviewing the following output from file integrity monitoring software installed on a very busy server at a large service provider. The server has not been updated since it was installed. Drag and drop the log entry that identifies the first instance of server compromise.

SY0-501 Part 29 Q04 081 Question 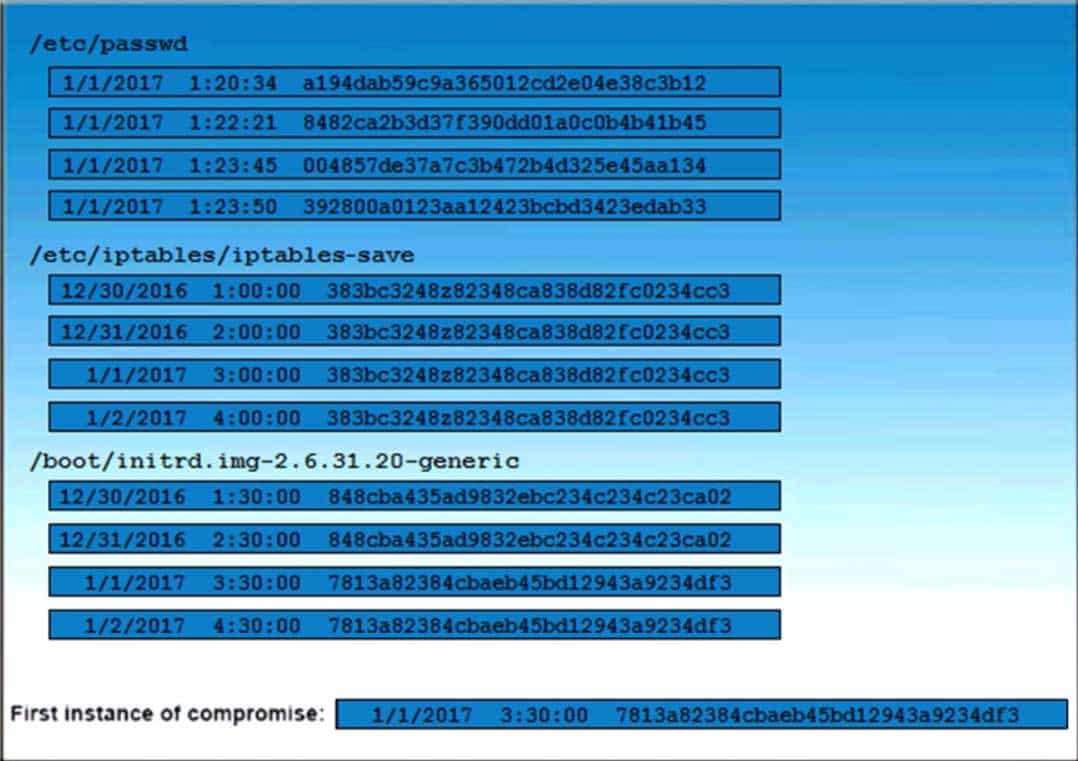
SY0-501 Part 29 Q04 081 Answer -
DRAG DROP
A security administrator has been tasked with implementing controls that meet management goals. Drag and drop the appropriate control used to accomplish the account management goal. Options may be used once or not at all.

SY0-501 Part 29 Q05 082 Question 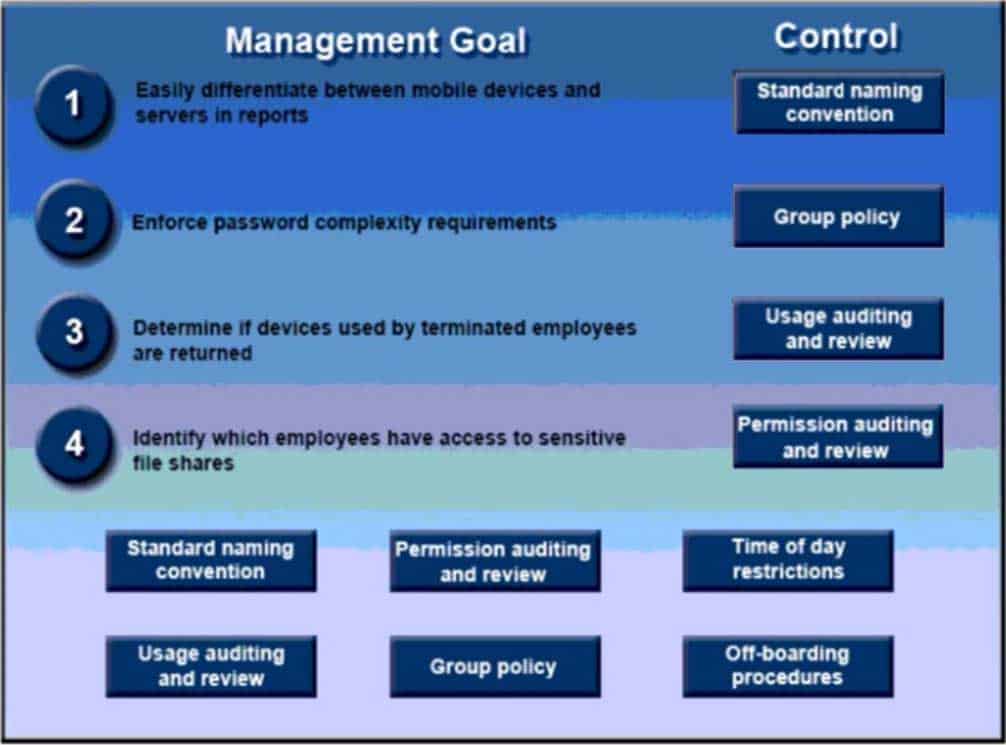
SY0-501 Part 29 Q05 082 Answer -
Joe, a backup administrator, wants to implement a solution that will reduce the restoration time of physical servers. Which of the following is the BEST method for Joe to use?
- Differential
- Incremental
- Full
- Snapshots
-
Which of the following development models entails several iterative and incremental software development methodologies such as Scrum?
- Spiral
- Waterfall
- Agile
- Rapid
-
Which of the following are used to substantially increase the computation time required to crack a password? (Choose two.)
- BCRYPT
- Substitution cipher
- ECDHE
- PBKDF2
- Diffie-Hellman
-
Which of the following describes the maximum amount of time a mission essential function can operate without the systems it depends on before significantly impacting the organization?
- MTBF
- MTTR
- RTO
- RPO
-
A network administrator is brute forcing accounts through a web interface. Which of the following would provide the BEST defense from an account password being discovered?
- Password history
- Account lockout
- Account expiration
- Password complexity
-
A security engineer wants to add SSL to the public web server. Which of the following would be the FIRST step to implement the SSL certificate?
- Download the web certificate
- Install the intermediate certificate
- Generate a CSR
- Encrypt the private key
-
Which of the following is a major difference between XSS attacks and remote code exploits?
- XSS attacks use machine language, while remote exploits use interpreted language
- XSS attacks target servers, while remote code exploits target clients
- Remote code exploits aim to escalate attackers’ privileges, while XSS attacks aim to gain access only
- Remote code exploits allow writing code at the client side and executing it, while XSS attacks require no code to work
-
An employee workstation with an IP address of 204.211.38.211/24 reports it is unable to submit print jobs to a network printer at 204.211.38.52/24 after a firewall upgrade. The active firewall rules are as follows:

SY0-501 Part 29 Q13 083 Assuming port numbers have not been changed from their defaults, which of the following should be modified to allow printing to the network printer?
- The permit statement for 204.211.38.52/24 should be changed to TCP port 631 instead of UDP
- The deny statement for 204.211.38.52/24 should be changed to a permit statement
- The permit statement for 204.211.38.52/24 should be changed to UDP port 443 instead of 631
- The permit statement for 204.211.38.211/24 should be changed to TCP port 631 only instead of ALL
-
A security analyst is doing a vulnerability assessment on a database server. A scanning tool returns the following information:

SY0-501 Part 29 Q14 084 There have been several security breaches on the web server that accesses this database. The security team is instructed to mitigate the impact of any possible breaches. The security team is also instructed to improve the security on this database by making it less vulnerable to offline attacks. Which of the following would BEST accomplish these goals? (Choose two.)
- Start using salts to generate MD5 password hashes
- Generate password hashes using SHA-256
- Force users to change passwords the next time they log on
- Limit users to five attempted logons before they are locked out
- Require the web server to only use TLS 1.2 encryption
-
A systems administrator has implemented multiple websites using host headers on the same server. The server hosts two websites that require encryption and other websites where encryption is optional. Which of the following should the administrator implement to encrypt web traffic for the required websites?
- Extended domain validation
- TLS host certificate
- OCSP stapling
- Wildcard certificate
-
Which of the following are considered among the BEST indicators that a received message is a hoax? (Choose two.)
- Minimal use of uppercase letters in the message
- Warnings of monetary loss to the receiver
- No valid digital signature from a known security organization
- Claims of possible damage to computer hardware
- Embedded URLs
-
Management wishes to add another authentication factor in addition to fingerprints and passwords in order to have three-factor authentication. Which of the following would BEST satisfy this request?
- Retinal scan
- Passphrase
- Token fob
- Security question
-
During a lessons learned meeting regarding a previous incident, the security team receives a follow-up action item with the following requirements:
– Allow authentication from within the United States anytime
– Allow authentication if the user is accessing email or a shared file system
– Do not allow authentication if the AV program is two days out of date
– Do not allow authentication if the location of the device is in two specific countriesGiven the requirements, which of the following mobile deployment authentication types is being utilized?
- Geofencing authentication
- Two-factor authentication
- Context-aware authentication
- Biometric authentication
-
A network administrator is creating a new network for an office. For security purposes, each department should have its resources isolated from every other department but be able to communicate back to central servers. Which of the following architecture concepts would BEST accomplish this?
- Air gapped network
- Load balanced network
- Network address translation
- Network segmentation
-
A customer calls a technician and needs to remotely connect to a web server to change some code manually. The technician needs to configure the user’s machine with protocols to connect to the Unix web server, which is behind a firewall. Which of the following protocols does the technician MOST likely need to configure?
- SSH
- SFTP
- HTTPS
- SNMP