21.2.10 Optional Lab – Configure ASA Basic Settings Using the CLI Answers
Optional Lab – Configure ASA Basic Settings Using CLI (Answers Version)
Answers Note: Red font color or gray highlights indicate text that appears in the instructor copy only.
Topology
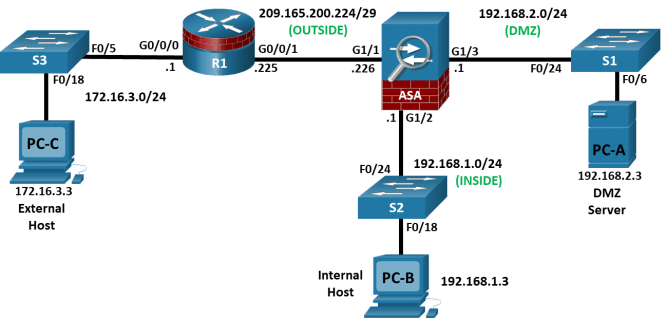
Addressing Table
|
Device |
Interface |
IP Address |
Subnet Mask |
Default Gateway |
Switch Port |
|
R1 |
G0/0/0 |
172.16.3.1 |
255.255.255.0 |
N/A |
S3 F0/5 |
|
R1 |
G0/0/1 |
209.165.200.225 |
255.255.255.248 |
ASA G1/1 |
|
|
ASA |
G1/1 (OUTSIDE) |
209.165.200.226 |
255.255.255.248 |
N/A |
R1 G0/0/1 |
|
ASA |
G1/2 (INSIDE) |
192.168.1.1 |
255.255.255.0 |
N/A |
S2 F0/24 |
|
ASA |
G1/3 (DMZ) |
192.168.2.1 |
255.255.255.0 |
N/A |
S1 F0/24 |
|
PC-A |
NIC |
192.168.2.3 |
255.255.255.0 |
192.168.2.1 |
S1 F0/6 |
|
PC-B |
NIC |
192.168.1.3 |
255.255.255.0 |
192.168.1.1 |
S2 F0/18 |
|
PC-C |
NIC |
172.16.3.3 |
255.255.255.0 |
172.16.3.1 |
S3 F0/18 |
Blank Line – no additional information
Objectives
Part 1: Configure Basic Device Settings
Part 2: Access the ASA Console and Use CLI Setup Mode to Configure Basic Settings
Part 3: Configure Basic ASA Settings and Interface Security Levels
Background / Scenario
The Cisco Adaptive Security Appliance (ASA) is an advanced network security device that integrates a stateful firewall, VPN, and FirePOWER services. This lab employs an ASA 5506-X to create a firewall and protect an internal corporate network from external intruders while allowing internal hosts access to the Internet. The ASA creates three security interfaces: OUTSIDE, INSIDE, and DMZ. It provides outside users limited access to the DMZ and no access to inside resources. Inside users can access the DMZ and outside resources.
The focus of this lab is to configure the ASA as a basic firewall. Other devices will receive minimal configuration to support the ASA portion of this lab. This lab uses the ASA CLI, which is similar to the IOS CLI, to configure basic device and security settings.
In Part 1 of this lab, you will configure the topology and non-ASA devices. In Part 2, you will explore two ways to configure basic ASA settings. In Part 3, you will configure additional settings, test connectivity, and configure Adaptive Security Device Manager (ASDM) access. ASDM provides an intuitive, GUI-based tool for configuring the ASA.
Note: The routers used with hands-on labs are Cisco 4221 with Cisco IOS XE Release 16.9.6 (universalk9 image). The switches used in the labs are Cisco Catalyst 2960+ with Cisco IOS Release 15.2(7) (lanbasek9 image). Other routers, switches, and Cisco IOS versions can be used. Depending on the model and Cisco IOS version, the commands available and the output produced might vary from what is shown in the labs. Refer to the Router Interface Summary Table at the end of the lab for the correct interface identifiers.
The ASA used with this lab is a Cisco model 5506-X with an 8-port integrated switch, running OS version 9.15(1), Adaptive Security Device Manager (ASDM) version 7.15(1).
Note: Before you begin, ensure that the devices have been erased and have no startup configurations.
Required Resources
1 Router (Cisco 4221 with Cisco XE Release 16.9.6 universal image or comparable with a Security Technology Package license)
3 Switches (Cisco 2960+ with Cisco IOS Release 15.2(7) lanbasek9 image or comparable)
3 PCs (Windows OS with a terminal emulation, such as PuTTY or Tera Term installed)
1 ASA 5506-X (OS version 9.15(1) and ASDM version 7.15(1) and Base license or comparable)
Console cables to configure Cisco networking devices
Ethernet cables as shown in the topology
Instructions
Part 1:Configure Basic Device Settings
In this part, you will set up the network topology and configure basic settings on the routers, such as interface IP addresses and static routing.
Note: Do not configure ASA settings at this time.
Step 1:Cable the network and clear previous device settings.
Attach the devices that are shown in the topology diagram and cable as necessary. Make sure the router and ASA have been erased and have no startup configuration.
Note: To avoid using the switches, use a cross-over cable to connect the end devices
Step 2:Configure R1 and the end devices.
- Use the following script to configure R1. No additional configuration for R1 will be required for this lab.
Note: R1 does not need any routing as all inbound packets from the ASA will have 209.165.200.226 as the source IP address.
R1 Script
enable
configure terminal
hostname R1
security passwords min-length 10
enable secret algorithm-type scrypt cisco12345
ip domain name netsec.com
username admin01 algorithm-type scrypt secret cisco12345
interface GigabitEthernet0/0/0
ip address 172.16.3.1 255.255.255.0
no shutdown
interface GigabitEthernet0/0/1
ip address 209.165.200.225 255.255.255.248
no shutdown
crypto key generate rsa general-keys modulus 1024
ip http server
line con 0
exec-timeout 5 0
logging synchronous
login local
line vty 0 4
exec-timeout 5 0
login local
transport input ssh
end
copy running start
- Configure a static IP address, subnet mask, and default gateway for PC-A, PC-B, and PC-C as shown in the IP Addressing Table.
Step 3:Verify connectivity.
Because the ASA is the focal point for the network zones, and it has not yet been configured, there will be no connectivity between devices that are connected to it. However, PC-C should be able to ping the R1 interface. From PC-C, ping the R1 G0/0/1 IP address (209.165.200.225). If these pings are not successful, troubleshoot the basic device configurations before continuing.
Part 2:Access the ASA Console and Use CLI Setup to Configure Basic Settings
In this part, you will access the ASA via the console and use various show commands to determine hardware, software, and configuration settings. You will clear the current configuration and use the CLI interactive setup utility to configure basic ASA settings.
Step 1:Access the ASA console.
- Accessing the ASA via the console port is the same as with a Cisco router or switch. Connect to the ASA console port with a rollover cable and use a terminal emulation program, such as TeraTerm or PuTTy to open a serial connection and access the CLI.
- The ASA initially prompts you to pre-configure the firewall using an interactive prompt. We will not be configuring the ASA this way, therefore enter no and press Enter. If you have inadvertently started the setup wizard, press CTRL-Z to exit it. The terminal screen should display the default ASA user EXEC hostname and prompt ciscoasa>.
- You will get prompt requesting that you configure an enable password to enter privileged EXEC mode. Enter class to configure the password and then again to confirm it. You will now be in privileged EXEC mode.
enable password cannot be removed
Enter Password: class
Repeat Password: class
Note: Save your configuration so that the password persists across reboots
(“write memory” or “copy running-config startup-config”).
ciscoasa#
Step 2:Determine the ASA version, interfaces, and license.
The ASA 5506-X comes with an integrated eight-port Ethernet switch. Ports G1/1 to G1/8 are normal GigabitEthernet ports.
Use the show version command to determine various aspects of this ASA device.
ciscoasa# show version
Cisco Adaptive Security Appliance Software Version 9.15(1)1
SSP Operating System Version 2.9(1.131)
Device Manager Version 7.15(1)
Compiled on Fri 20-Nov-20 18:47 GMT by builders
System image file is “disk0:/asa9-15-1-1-lfbff-k8.SPA”
Config file at boot was “startup-config”
ciscoasa up 2 days 23 hours
Hardware:ASA5506, 4096 MB RAM, CPU Atom C2000 series 1250 MHz, 1 CPU (4 cores)
Internal ATA Compact Flash, 8000MB
BIOS Flash M25P64 @ 0xfed01000, 16384KB
Encryption hardware device : Cisco ASA Crypto on-board accelerator (revision 0x1)
Number of accelerators: 1
1: Ext: GigabitEthernet1/1: address is 00a3.8ecd.0ed2, irq 255
2: Ext: GigabitEthernet1/2: address is 00a3.8ecd.0ed3, irq 255
3: Ext: GigabitEthernet1/3: address is 00a3.8ecd.0ed4, irq 255
<output omitted>
Questions:
What software version is this ASA running?
Type your answers here.
The ASA in this lab uses version 9.15(1).
What is the name of the system image file and from where was it loaded?
Type your answers here.
The system image file in the ASA for this lab is asa9-15-1-1-lfbff-k8.SPA, and it was loaded from disk0: (or flash:).
The ASA can be managed using a built-in GUI known as ASDM. What version of ASDM is this ASA running?
Type your answers here.
The ASA in this lab uses ASDM version 7.15(1).
What is the Firepower Extension Operating System version?
Type your answers here.
The Firepower-X version in this lab is 02.9(1.131).
How much RAM does this ASA have?
Type your answers here.
The ASA in this lab has 4096 MB RAM.
How much flash memory does this ASA have?
Type your answers here.
The ASA in this lab has 8000 MB RAM.
How many Ethernet ports does this ASA have?
Type your answers here.
The ASA in this lab has eight GigabitEthernet ports and a Management port.
What type of license does this ASA have?
Type your answers here.
The ASA has either Base or the Security Plus license.
Step 3:Determine the file system and contents of flash memory.
- Display the ASA file system using the show file system command. Determine what prefixes are supported.
ciscoasa# show file system
File Systems:
Size(b)Free(b)TypeFlagsPrefixes
* 73654722563859148800diskrwdisk0: flash:
––diskrwdisk1:
––networkrwtftp:
––opaquerwsystem:
––networkrohttp:
––networkrohttps:
––networkrwscp:
––networkrwftp:
––networkwocluster:
––stubrocluster_trace:
––networkrwsmb:
Question:
What is another name for flash:?
Type your answers here.
disk0:
- Display the contents of flash memory using either the show flash, show disk0, dir flash:, or dir disk0: command. These commands display similar output.
ciscoasa# show flash
–#––length–—–date/time——path
2838925172Jan 24 2021 20:50:06asdm-7151.bin
2933Feb 09 2021 11:43:44.boot_string
44096Jan 24 2021 20:52:44log
3531000Oct 28 2020 13:46:04log/asa-appagent.log
52265Feb 19 2021 15:25:22log/asa-cmd-server.log
144096Aug 29 2017 14:26:24crypto_archive
154096Aug 29 2017 14:26:28coredumpinfo
1659Aug 29 2017 14:26:28coredumpinfo/coredump.cfg
3135209829Oct 04 2017 03:17:02anyconnect-win-4.5.02033-webdeploy-k9.pkg
3270744710Oct 28 2020 22:31:52anyconnect-win-4.9.03049-webdeploy-k9.pkg
33137859680Jan 24 2021 20:47:30asa9-15-1-1-lfbff-k8.SPA
639Feb 19 2021 15:25:23snortpacketinfo.conf
7365472256 bytes total (3859148800 bytes free)
Question:
What is the name of the ASDM file in flash:?
Type your answers here.
asdm-7151.bin
Answers Note: Your ASA may display other files. Check the content of flash memory occasionally to see if there are FSCK*.REC files. These files are generated automatically by the ASA when it runs the file system check (fsck). You can delete these files by issuing the command delete flash:FSCK*.REC from the privileged EXEC promp. Press Enter at each prompt to confirm the deletion.
ciscoasa# delete flash:FSCK*.REC
Delete filename [FSCK*.REC]? <Enter>
Delete disk0:/FSCK0000.REC? [confirm] <Enter>
<output omitted>
Step 4:Determine the current running configuration.
The ASA 5506-X is commonly used as an edge security device that connects a small business or teleworker to an ISP device, such as a DSL or cable modem, for access to the internet.
- Display the current running configuration using the show running-config command.
ciscoasa# show running-config
: Saved
:
: Serial Number: JAD21140GC5
: Hardware:ASA5506, 4096 MB RAM, CPU Atom C2000 series 1250 MHz, 1 CPU (4 cores)
:
ASA Version 9.15(1)1
!
hostname ciscoasa
enable password ***** pbkdf2
service-module 1 keepalive-timeout 4
service-module 1 keepalive-counter 6
service-module sfr keepalive-timeout 4
service-module sfr keepalive-counter 6
names
no mac-address auto
!
interface GigabitEthernet1/1
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/2
<output omitted>
Note: To stop the output from a command using the CLI, press Q.
You may also see other security features, such as a global policy that inspects selected application traffic, which the ASA inserts by default if the original startup configuration has been erased. The actual output varies depending on the ASA model, version, and configuration status.
- You can restore the ASA to its factory default settings by using the configure factory-default global configuration command.When entering global configuration, you will initially be prompted to enable anonymous error reporting. Enter N, otherwise enter A to be prompted for this at a later date.
ciscoasa# conf t
ciscoasa(config)#
***************************** NOTICE *****************************
Help to improve the ASA platform by enabling anonymous reporting,
which allows Cisco to securely receive minimal error and health
information from the device. To learn more about this feature,
please visit: http://www.cisco.com/go/smartcall
Would you like to enable anonymous error reporting to help improve
the product? [Y]es, [N]o, [A]sk later: N
In the future, if you would like to enable this feature,
issue the command “call-home reporting anonymous”.
Please remember to save your configuration.
ciscoasa(config)# configure factory-default
Based on the inside IP address and mask, the DHCP address
pool size is reduced to 250 from the platform limit 256
WARNING: The boot system configuration will be cleared.
The first image found in disk0:/ will be used to boot the
system on the next reload.
Verify there is a valid image on disk0:/ or the system will
not boot.
Begin to apply factory-default configuration:
Clear all configuration
Executing command: !
Executing command: interface Management1/1
Executing command:management-only
Executing command:no nameif
Executing command:no security-level
Executing command:no ip address
Executing command:no shutdown
Executing command:exit
Executing command: !
Executing command: interface GigabitEthernet1/1
Executing command:nameif outside
INFO: Security level for “outside” set to 0 by default.
Executing command:security-level 0
Executing command:no shutdown
<output omitted>
Executing command: same-security-traffic permit inter-interface
Executing command: !
Executing command: !
Factory-default configuration is completed
ciscoasa(config)#
- You may want to capture and print the factory-default configuration as a reference. Use the terminal emulation program to copy it from the ASA and paste it into a text document. You can then edit this file if desired, so that it contains only valid commands. You should remove password commands and enter the no shut command to enable the desired interfaces.
Step 5:Clear the previous ASA configuration settings.
- Use the write erase command to remove the startup-config file from flash memory.
ciscoasa(config)# end
ciscoasa# write erase
Erase configuration in flash memory? [confirm] <Enter>
[OK]
ciscoasa# show start
No Configuration
ciscoasa#
Note: The IOS command erase startup-config is not supported on the ASA.
- Use the reload command to restart the ASA. This causes the ASA to come up in CLI Setup mode. If prompted that the config has been modified and needs to be saved, respond with N, and then press Enter to proceed with the reload.
ciscoasa# reload
System config has been modified. Save? [Y]es/[N]o:n
Proceed with reload? [confirm] <Enter>
ciscoasa#
***
*** — START GRACEFUL SHUTDOWN —
Shutting down isakmp
Shutting down webvpn
Shutting down sw-module
Shutting down License Controller
Shutting down File system
<output omitted>
Step 6:Use the Setup interactive CLI mode to configure basic settings.
When the ASA completes the reload process, it should detect that the startup-config file is missing and prompt you to pre-configure the firewall using interactive prompts. This presents a series of interactive prompts to configure basic ASA settings.
Note: The interactive prompt mode does not configure the ASA with factory defaults as described in Step 4. This mode can be used to configure minimal basic settings, such as hostname, clock, and passwords. You can also go directly to the CLI to configure the ASA settings, as described in Part 3.
- Respond to the Setup interactive prompts as shown here, after the ASA reloads.
Pre-configure Firewall now through interactive prompts [yes]? <Enter>
Firewall Mode [Routed]: <Enter>
Enable password [<use current password>]: class
Allow password recovery [yes]? <Enter>
Clock (UTC): <Enter>
Year [2021]: <Enter>
Month [Feb]: <Enter>
Day [22]: <Enter>
Time [15:16:32]: <Enter>
Management IP address: 192.168.100.1
Management network mask: 255.255.255.0
Host name: ASA-Init
Domain name: generic.com
IP address of host running Device Manager: <Enter>
The following configuration will be used:
Enable password: class
Allow password recovery: yes
Clock (UTC): 07:29:14 Mar 19 2019
Firewall Mode: Routed
Management IP address: 192.168.100.1
Management network mask: 255.255.255.0
Host name: ASA-Init
Domain name: generic.com
Use this configuration and save to flash? [yes] <Enter>
INFO: Security level for “management” set to 0 by default.
Cryptochecksum: d0b22e76 5178e9e6 0a6bc590 5f5e5a3d
3958 bytes copied in 0.80 secs
User enable_1 logged in to ASA-Init
Logins over the last 1 days: 1.
Failed logins since the last login: 0.
Type help or ‘?’ for a list of available commands.
ASA-Init>
Note: In the above configuration, the IP address of the host running ASDM was left blank. It is not necessary to install ASDM on a host. It can be run from the flash memory of the ASA device itself using the browser of the host.
Note: The responses to the prompts are automatically stored in the startup-config and the running config. However, additional security–related commands, such as the policy-map global_policy that uses class inspection_default, are inserted into the running-config by the ASA OS.
- Enter privileged EXEC mode with the enable command. Enter class for the password.
- Issue the show run command to see the additional security-related configuration commands that are inserted by the ASA.
- Issue the write memory command to capture the additional security-related commands in the startup-config file.
Part 3:Configure ASA Settings and Interface Security
In this part, you will configure basic settings by using the ASA CLI, even though some of them were already configured using the Setup mode interactive prompts in the previous part. In this part, you will start with the settings configured in the previous part and then add to or modify them to create a complete basic configuration.
Tip: Many ASA CLI commands are similar to, if not the same, as those used with the Cisco IOS CLI. In addition, the process of moving between configuration modes and sub-modes is essentially the same.
Note: You must complete the previous part before beginning this part.
Step 1:Configure the hostname and domain name.
- Enter global configuration mode using the config t command. The first time you enter configuration mode after running Setup, you will be prompted to enable anonymous reporting. Respond with no.
ASA-Init# config t
ASA-Init(config)#
***************************** NOTICE *****************************
Help to improve the ASA platform by enabling anonymous reporting,
which allows Cisco to securely receive minimal error and health
information from the device. To learn more about this feature,
please visit: http://www.cisco.com/go/smartcall
Would you like to enable anonymous error reporting to help improve
the product? [Y]es, [N]o, [A]sk later: n
In the future, if you would like to enable this feature,
issue the command “call-home reporting anonymous”.
Please remember to save your configuration.
- Configure the ASA hostname using the hostname command.
ASA-Init(config)# hostname NETSEC-ASA
- Configure the domain name using the domain-name command.
NETSEC-ASA(config)# domain-name netsec.com
Step 2:Configure the login and enable mode passwords.
- The login password is used for Telnet connections (and SSH prior to ASA version 8.4). By default, it is set to cisco, but because the default startup configuration was erased you have the option to configure the login password using the passwd or password command. This command is optional because later in the lab we will configure the ASA for SSH, and not Telnet access.
NETSEC-ASA(config)# passwd cisco
- Configure the privileged EXEC mode (enable) password using the enable password command.
NETSEC-ASA(config)# enable password class
Step 3:Set the date and time.
The date and time can be set manually using the clock set command. The syntax for the clock set command is clock set hh:mm:ss {month day | day month} year. The following example shows how to set the date and time using a 24-hour clock:
NETSEC-ASA(config)# clock set 2:23:00 feb 22 2021
Step 4:Configure the INSIDE and OUTSIDE interfaces.
In this step, you will configure internal and external interfaces, name them, assign IP addresses, and set the interface security level.
In Part 2, the MGMT interface was configured with an IP address of 192.168.100.1. You will configure another interface as the INSIDE interface for this lab and remove the IP addressing for M1/1. You will only configure the INSIDE and OUTSIDE interfaces at this time. The DMZ interface will be configured in the next lab.
- Configure interface G1/2 for the INSIDE network, 192.168.1.0/24. Name the interface INSIDE, set the security level to the highest setting of 100 and enable it.
NETSEC-ASA(config)# interface g1/2
NETSEC-ASA(config-if)# nameif INSIDE
NETSEC-ASA(config-if)# ip address 192.168.1.1 255.255.255.0
NETSEC-ASA(config-if)# security-level 100
NETSEC-ASA(config-if)# no shutdown
- Configure interface G1/1for the OUTSIDE network, 209.165.200.224/29. Name the interface OUTSIDE, set the security level to the lowest setting of 0 and enable it.
NETSEC-ASA(config-if)# interface g1/1
NETSEC-ASA(config-if)# nameif OUTSIDE
NETSEC-ASA(config-if)# ip address 209.165.200.226 255.255.255.248
NETSEC-ASA(config-if)# security-level 0
NETSEC-ASA(config-if)# no shutdown
- Remove the configuration from the M1/1 interface and shut it down (if required).
NETSEC-ASA(config-if)# interface m1/1
NETSEC-ASA(config-if)# shutdown
NETSEC-ASA(config-if)# no ip address
Interface security-level notes:
You may receive a message that the security level for the INSIDE interface was set automatically to 100, and the OUTSIDE interface was set to 0. The ASA uses interface security levels from 0 to 100 to enforce the security policy. Security level 100 (INSIDE) is the most secure and level 0 (OUTSIDE) is the least secure.
By default, the ASA applies a policy where traffic from a higher security level interface to one with a lower level is permitted and traffic from a lower security level interface to one with a higher security level is denied. The ASA default security policy permits outbound traffic, which is inspected, by default. Returning traffic is allowed due to stateful packet inspection. This default “routed mode” firewall behavior of the ASA allows packets to be routed from the INSIDE network to the OUTSIDE network, but not vice-versa. In a latter part of this lab, you will configure NAT to increase the firewall protection.
- Display the status for all ASA interfaces using the show interface ip brief command.
Note: The command syntax is different from the show ip interface brief IOS command. If any of the physical or logical interfaces previously configured are not up/up, troubleshoot as necessary before continuing.
Tip: Most ASA show commands, as well as ping, copy, and others, can be issued from within any configuration mode prompt without the do command that is required with IOS.
NETSEC-ASA(config-if)# show interface ip brief
InterfaceIP-AddressOK? Method StatusProtocol
Virtual0127.1.0.1YES unsetupup
GigabitEthernet1/1209.165.200.226 YES manual upup
GigabitEthernet1/2192.168.1.1YES manual upup
GigabitEthernet1/3unassignedYES unsetadministratively down down
GigabitEthernet1/4unassignedYES unsetadministratively down down
GigabitEthernet1/5unassignedYES unsetadministratively down down
GigabitEthernet1/6unassignedYES unsetadministratively down down
GigabitEthernet1/7unassignedYES unsetadministratively down down
GigabitEthernet1/8unassignedYES unsetadministratively down down
Internal-Control1/1unassignedYES unsetdowndown
Internal-Data1/1unassignedYES unsetdowndown
Internal-Data1/2unassignedYES unsetdowndown
Internal-Data1/3unassignedYES unsetupup
Internal-Data1/4169.254.1.1YES unsetupup
Management1/1unassignedYES unsetadministratively down down
- Display the Layer 3 interface information using the show ip address command.
NETSEC-ASA(config-if)# show ip address
System IP Addresses:
InterfaceNameIP addressSubnet maskMethod
GigabitEthernet1/1OUTSIDE209.165.200.226 255.255.255.248 manual
GigabitEthernet1/2INSIDE192.168.1.1255.255.255.0manual
Current IP Addresses:
InterfaceNameIP addressSubnet maskMethod
GigabitEthernet1/1OUTSIDE209.165.200.226 255.255.255.248 manual
GigabitEthernet1/2INSIDE192.168.1.1255.255.255.0manual
- You may also use the command show running-config interface to display the configuration for a particular interface from the running-config.
NETSEC-ASA(config-if)# show run interface g1/1
!
interface GigabitEthernet1/1
nameif OUTSIDE
security-level 0
ip address 209.165.200.226 255.255.255.248
Step 5:Test connectivity to the ASA.
- Ensure that PC-B has a static IP address of 192.168.1.3, a subnet mask of 255.255.255.0, and a default gateway of 192.168.1.1.
- You should be able to ping from PC-B to the ASA INSIDE interface address and ping from the ASA to PC-B. If the pings fail, troubleshoot the configuration as necessary.
NETSEC-ASA(config-if)# ping 192.168.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/10 ms
- From PC-C, ping the OUTSIDE interface IP address 209.165.200.226. Alternatively, instead of configuring PC-C just for a ping test, you can source a ping from the G0/0/0 interface on R1. You should not be able to ping the OUTSIDE interface.
R1# ping 209.165.200.226 source 172.16.3.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 209.165.200.226, timeout is 2 seconds:
Packet sent with a source address of 172.16.3.1
…..
Success rate is 0 percent (0/5)
R1#
Step 6:Configure ASDM access to the ASA.
ASDM provides an intuitive, GUI-based tool for configuring the ASA from a PC.
- Configure the ASA to allow HTTPS connections from any host on the INSIDE network (192.168.1.0/24) using the http server enable command in global configuration mode. This allows access to the ASA GUI (ASDM).
NETSEC-ASA(config-if)# exit
NETSEC-ASA(config)# http server enable
NETSEC-ASA(config)# http 192.168.1.0 255.255.255.0 INSIDE
- Open a browser on PC-B and test the HTTPS access to the ASA by entering https://192.168.1.1. You will be prompted that the connection is not secure. Select the option to allow you to continue to the webpage.
- You should then see Cisco ASDM Welcome screen that allows you to either Install ASDM Launcher or Install Java Web Start to run ASDM as a Java Web start application.
Note: If you or your instructor have already installed the Cisco ASDM-ID Launcher, open the application.
- You should then be required to authenticate to the ASA. Because no username was specified, simply enter the enable password class in the password field.
- Close the browser or Cisco ASDM-ID Launcher. Using ASDM to configure the ASA is beyond the scope of this course. However, there is an optional topic after the summary for this module with more information about ASDM along with three optional labs. The objective here is not to use the ASDM configuration screens, but to verify HTTP/ASDM connectivity to the ASA. If you are unable to access ASDM, check your configurations.If the configurations are correct contact your instructor for further assistance.
Step 7:Save your ASA configuration for the next lab.
In the next lab, you will extend your current configuration adding a DMZ, routing, NAT, DHCP, AAA, and SSH. If you are ready now, proceed to that lab. If not, save you configurations to load into the next lab.
Router Interface Summary Table
|
Router Model |
Ethernet Interface #1 |
Ethernet Interface #2 |
Serial Interface #1 |
Serial Interface #2 |
|
1900 |
Gigabit Ethernet 0/0 (G0/0) |
Gigabit Ethernet 0/1 (G0/1) |
Serial 0/0/0 (S0/0/0) |
Serial 0/0/1 (S0/0/1) |
|
2900 |
Gigabit Ethernet 0/0 (G0/0) |
Gigabit Ethernet 0/1 (G0/1) |
Serial 0/0/0 (S0/0/0) |
Serial 0/0/1 (S0/0/1) |
|
4221 |
Gigabit Ethernet 0/0/0 (G0/0/0) |
Gigabit Ethernet 0/0/1 (G0/0/1) |
Serial 0/1/0 (S0/1/0) |
Serial 0/1/1 (S0/1/1) |
|
4300 |
Gigabit Ethernet 0/0/0 (G0/0/0) |
Gigabit Ethernet 0/0/1 (G0/0/1) |
Serial 0/1/0 (S0/1/0) |
Serial 0/1/1 (S0/1/1) |
Blank Line, No additional information
Note: To find out how the router is configured, look at the interfaces to identify the type of router and how many interfaces the router has. There is no way to effectively list all the combinations of configurations for each router class. This table includes identifiers for the possible combinations of Ethernet and Serial interfaces in the device. The table does not include any other type of interface, even though a specific router may contain one. An example of this might be an ISDN BRI interface. The string in parenthesis is the legal abbreviation that can be used in Cisco IOS commands to represent the interface.
Device Configs (Final)
NETSEC-ASA (5506-X)
NETSEC-ASA# show run
: Saved
:
: Serial Number: JAD21140GC5
: Hardware:ASA5506, 4096 MB RAM, CPU Atom C2000 series 1250 MHz, 1 CPU (4 cores)
:
ASA Version 9.15(1)1
!
hostname NETSEC-ASA
domain-name netsec.com
enable password ***** pbkdf2
service-module 1 keepalive-timeout 4
service-module 1 keepalive-counter 6
service-module sfr keepalive-timeout 4
service-module sfr keepalive-counter 6
passwd ***** encrypted
names
no mac-address auto
!
interface GigabitEthernet1/1
nameif OUTSIDE
security-level 0
ip address 209.165.200.226 255.255.255.248
!
interface GigabitEthernet1/2
nameif INSIDE
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface GigabitEthernet1/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/5
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/6
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/7
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/8
shutdown
no nameif
no security-level
no ip address
!
interface Management1/1
management-only
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
dns server-group DefaultDNS
domain-name netsec.com
pager lines 24
mtu OUTSIDE 1500
mtu INSIDE 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication login-history
http server enable
http 192.168.1.0 255.255.255.0 INSIDE
no snmp-server location
no snmp-server contact
service sw-reset-button
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpool policy
telnet timeout 5
ssh stricthostkeycheck
ssh timeout 5
ssh version 2
ssh key-exchange group dh-group14-sha256
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
dynamic-access-policy-record DfltAccessPolicy
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect snmp
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect ip-options
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:1e512ac27a6af8448674957167a00d22
: end
NETSEC-ASA#
Router R1
R1# show run
Building configuration…
Current configuration : 1389 bytes
!
! Last configuration change at 14:04:35 UTC Sun Jan 24 2021
!
version 16.9
service timestamps debug datetime msec
service timestamps log datetime msec
platform qfp utilization monitor load 80
platform punt-keepalive disable-kernel-core
!
hostname R1
!
boot-start-marker
boot-end-marker
!
!
security passwords min-length 10
enable secret 5 $1$IqzA$Yleqbiia3ztmP6txGC0KF.
!
no aaa new-model
!
ip domain name netsec.com
!
login on-success log
!
subscriber templating
!
multilink bundle-name authenticated
!
license udi pid ISR4221/K9 sn FGL23313183
no license smart enable
diagnostic bootup level minimal
!
spanning-tree extend system-id
!
username admin01 secret 9 $9$m1jhnk3g.tkrzF$gyTaS7FYmyJ3cy87mr40Yel6rs/NTqefCbXziAurHxg
!
redundancy
mode none
!
interface GigabitEthernet0/0/0
ip address 172.16.3.1 255.255.255.0
negotiation auto
!
interface GigabitEthernet0/0/1
ip address 209.165.200.225 255.255.255.248
negotiation auto
!
ip forward-protocol nd
ip http server
ip http secure-server
!
control-plane
!
line con 0
exec-timeout 0 0
logging synchronous
login local
transport input none
stopbits 1
line aux 0
stopbits 1
line vty 0 4
exec-timeout 5 0
login local
transport input ssh
!
end